The_Panda_Trueno
Dabbler
- Joined
- Nov 13, 2022
- Messages
- 39
EDIT: My bad, I sent this into the wrong category by accident.
Okay so, I was really about to break my laptop over this since I've been trying this for over 5 hours and am out of patience, so sorry if anything sounds a bit condescending:
I can't SSH at all into ANY of my servers with keys only. The goal here is to have key-only authentication for SSH because I need to open SSH publicly via a domain.
Also don't lecture me on how insecure it is to do that. I do not care.
This is what I did so far:
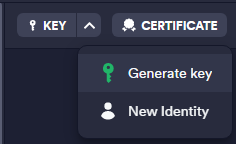
Went into Termius, and generated a key. So far, no issues.
I saw a post somewhere saying that since TrueNAS 13, RSA is deprecated. Since I use SCALE, I didn't know if it applied so I tried both RSA and ED25519:
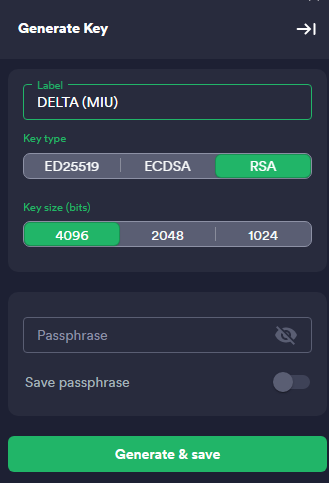
So far everything is fine.
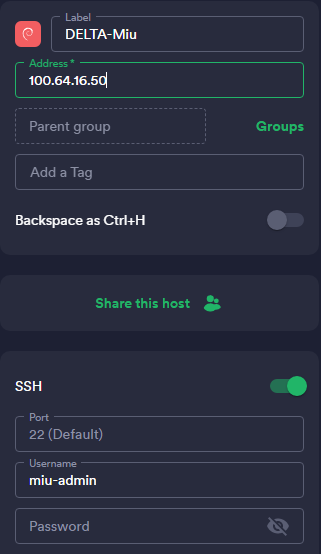
I input everything I need (username etc.) and connect selecting the key.
(Note: IP isn't public, no need to blur)
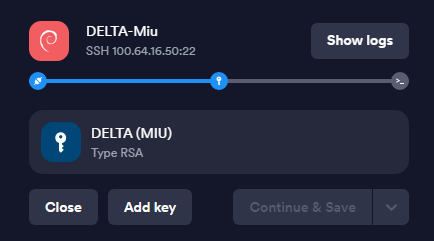
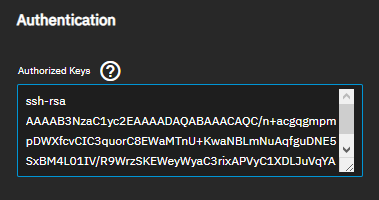
But then I get this no matter what I do on either the client side or server side:
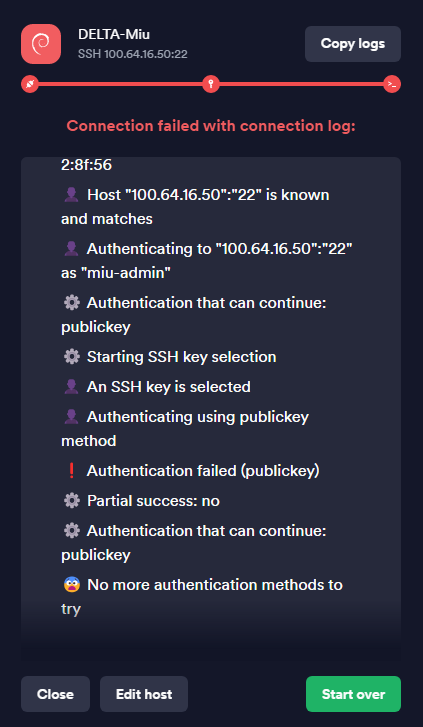
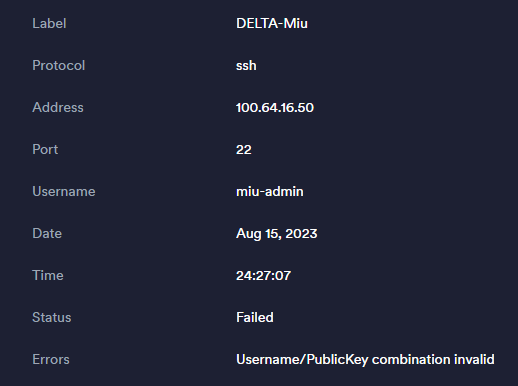
I get this from multiple clients, from multiple devices.
I then tried to verify that the file within .ssh did exist, and it did.
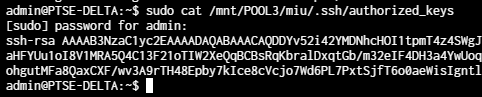
I also chown'd to the appropriate user (miu-admin) and chmod 600'd the file. I also tried 777, but it didn't work either and ain't the best thing to do anyway.
Stangely, as you might have seen in one of the screenshots, it says ''Username/PublicKey combination invalid''. I do not understand since I did specify to Termius to use the correct user to which the key is binded to.
Doing so on Windows' terminal with ''ssh miu-admin@100.64.16.50'' yields the same result.
What am I supposed to do ?
Okay so, I was really about to break my laptop over this since I've been trying this for over 5 hours and am out of patience, so sorry if anything sounds a bit condescending:
I can't SSH at all into ANY of my servers with keys only. The goal here is to have key-only authentication for SSH because I need to open SSH publicly via a domain.
Also don't lecture me on how insecure it is to do that. I do not care.
This is what I did so far:
Went into Termius, and generated a key. So far, no issues.
I saw a post somewhere saying that since TrueNAS 13, RSA is deprecated. Since I use SCALE, I didn't know if it applied so I tried both RSA and ED25519:
So far everything is fine.
I input everything I need (username etc.) and connect selecting the key.
(Note: IP isn't public, no need to blur)
But then I get this no matter what I do on either the client side or server side:
I get this from multiple clients, from multiple devices.
I then tried to verify that the file within .ssh did exist, and it did.
I also chown'd to the appropriate user (miu-admin) and chmod 600'd the file. I also tried 777, but it didn't work either and ain't the best thing to do anyway.
Stangely, as you might have seen in one of the screenshots, it says ''Username/PublicKey combination invalid''. I do not understand since I did specify to Termius to use the correct user to which the key is binded to.
Doing so on Windows' terminal with ''ssh miu-admin@100.64.16.50'' yields the same result.
What am I supposed to do ?