develissimo
Cadet
- Joined
- Mar 21, 2019
- Messages
- 6
Hi folks,
SHORT story:
years ago i thought it was a wise idea to separate connections (NFS, iSCSI, ...) via different IP addresses. So i did use the feature to ADD additional IP Addresses to a network interface.
DETAILED story:
We all know such setup (multiple IP addresses with overlapping or same subnet) could lead to problematic package routing.
But i thought:
Right now we do run "successfully" a Link Aggregation LAGG with LACP protocol having 3 Cat Cables attached since some years already. But the scenario is the same if you do not run a Link Aggregation but just add this multiple IP addresses to a single NIC.
FreeNAS/TrueNAS and the connected managed switch are reporting fine about the Link Aggregation as you can see here:
Switch screenshot - reporting LAGG is fine and active:
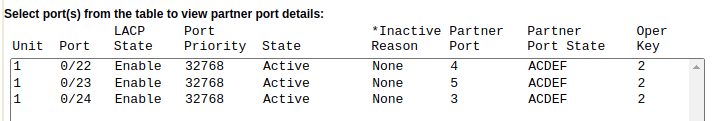
* switch device: HPE 1920-24G Switch JG924A
Output of command ifconfig:
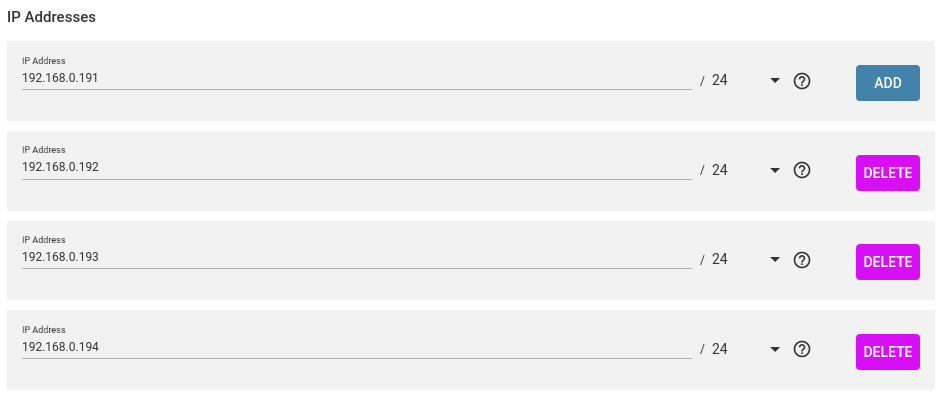
Multiple iSCSI and NFS connections are connected via the IP addresses 192.168.0.191 up to 192.168.0.194 without any recognized issues.
So far so good!
INFO: related to this post: can-lan-port-have-multiple-ip-addresses-of-same-subnet-mask-or-different-subnet
QUESTIONs:
Finally:
Thanks in advanced for your appreciated feedback.
Kind regards,
Raphael
SHORT story:
years ago i thought it was a wise idea to separate connections (NFS, iSCSI, ...) via different IP addresses. So i did use the feature to ADD additional IP Addresses to a network interface.
- I have been curious, but this setup seems to work fine.
!? I thought only IP addresses on different non overlapping subnets would be allowed... but that was not the case.
DETAILED story:
We all know such setup (multiple IP addresses with overlapping or same subnet) could lead to problematic package routing.
But i thought:
- Hey: "If the TrueNAS-Team allows us to set multiple IP addresses with same subnet to one single NIC, for sure this problem is solved by some technique" i tested it... it worked... and i did not investigate further.
Right now we do run "successfully" a Link Aggregation LAGG with LACP protocol having 3 Cat Cables attached since some years already. But the scenario is the same if you do not run a Link Aggregation but just add this multiple IP addresses to a single NIC.
FreeNAS/TrueNAS and the connected managed switch are reporting fine about the Link Aggregation as you can see here:
Switch screenshot - reporting LAGG is fine and active:
* switch device: HPE 1920-24G Switch JG924A
Output of command ifconfig:
Code:
ifconfig
re0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
description: member of lagg0
options=8209b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,VLAN_HWCSUM,WOL_MAGIC,LINKSTATE>
ether 30:9c:23:9e:05:b8
media: Ethernet autoselect (none)
status: no carrier
nd6 options=9<PERFORMNUD,IFDISABLED>
igb0: flags=8802<BROADCAST,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=e527bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,TSO4,TSO6,LRO,WOL_MAGIC,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6>
ether a0:36:9f:8a:0f:b0
media: Ethernet autoselect
status: no carrier
nd6 options=1<PERFORMNUD>
igb1: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
description: member of lagg0
options=e507bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,TSO4,TSO6,LRO,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6>
ether a0:36:9f:8a:0f:b1
media: Ethernet autoselect (1000baseT <full-duplex>)
status: active
nd6 options=9<PERFORMNUD,IFDISABLED>
igb2: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=e507bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,TSO4,TSO6,LRO,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6>
ether a0:36:9f:8a:0f:b1
hwaddr a0:36:9f:8a:0f:b2
media: Ethernet autoselect (1000baseT <full-duplex>)
status: active
nd6 options=1<PERFORMNUD>
igb3: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
description: member of lagg0
options=e507bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,TSO4,TSO6,LRO,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6>
ether a0:36:9f:8a:0f:b1
hwaddr a0:36:9f:8a:0f:b3
media: Ethernet autoselect (1000baseT <full-duplex>)
status: active
nd6 options=9<PERFORMNUD,IFDISABLED>
lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384
options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6>
inet6 ::1 prefixlen 128
inet6 fe80::1%lo0 prefixlen 64 scopeid 0x6
inet 127.0.0.1 netmask 0xff000000
groups: lo
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
pflog0: flags=0<> metric 0 mtu 33160
groups: pflog
lagg0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
description: lagg0
options=e507bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM,TSO4,TSO6,LRO,VLAN_HWFILTER,VLAN_HWTSO,RXCSUM_IPV6,TXCSUM_IPV6>
ether a0:36:9f:8a:0f:b1
inet 192.168.0.193 netmask 0xffffff00 broadcast 192.168.0.255
inet 192.168.0.191 netmask 0xffffff00 broadcast 192.168.0.255
inet 192.168.0.194 netmask 0xffffff00 broadcast 192.168.0.255
inet 192.168.0.192 netmask 0xffffff00 broadcast 192.168.0.255
laggproto lacp lagghash l2,l3,l4
laggport: igb1 flags=1c<ACTIVE,COLLECTING,DISTRIBUTING>
laggport: igb2 flags=1c<ACTIVE,COLLECTING,DISTRIBUTING>
laggport: igb3 flags=1c<ACTIVE,COLLECTING,DISTRIBUTING>
groups: lagg
media: Ethernet autoselect
status: active
nd6 options=9<PERFORMNUD,IFDISABLED>
Multiple iSCSI and NFS connections are connected via the IP addresses 192.168.0.191 up to 192.168.0.194 without any recognized issues.
So far so good!
INFO: related to this post: can-lan-port-have-multiple-ip-addresses-of-same-subnet-mask-or-different-subnet
- multiple IP addresses with SAME subnet are allowed.
- multiple IP addresses with OVERLAPPING subnets are disallowed.
- maybe there should be a hint on such overlapping subnets being discouraged!?
QUESTIONs:
- Is it wise to have multiple IP addresses with same subnet on LAGG or NIC-Interface? Wouldn't this lead to routing issues or performance impacts?
- Why was/is it allowed in FreeNAS/TrueNAS GUI to have multiple IP addresses with SAME subnet? How are they separated from each other? Is this a special technique? Will this lead to performance loss or routing issues?
- Why was/is it allowed in FreeNAS/TrueNAS GUI to have multiple IP addresses with overlapping subnets? How are they separated from each other? Is this a special technique? Will this lead to performance loss or routing errors?
- Is having multiple IP addresses with same subnet the proper way to achieve another little step of separation for NFS and iSCSI? Besides from authentication techniques such as CHAP for iSCSI and Authorized Hosts/Authorized IP addresses for NFS etc..
- What is the best way in TrueNAS to detect errors in package routing/network traffic?
Finally:
- So the INFO about overlapping but not identical subnets was just informative and we do not use such setup.
- The multiple IP Addresses with same subnet on the other hand is used actively in our setup and we are concerned if returning back to just one single IP address is advised.
Thanks in advanced for your appreciated feedback.
Kind regards,
Raphael
