Hi,
i am trying to setup a VPN gateway for my local LAN. I don`t want to connect from WAN to my network, i want to use the VPN-Tunnel in the Jail as gateway for my local devices, that don`t have a VPN option. The used Jail release version is 13.1-RELEASE-p5, VNET, BPF, allow_tun are enabled.
So for my understanding i need to setup a working WG tunnel in my Jail (already done!) and have to route the traffic through my jail`s IP from local network nat-ed to the WG IP. And for the routing i have use ipfw rules. A "kill-switch" if no VPN tunnel is active should be configured, too.
I tried several days now and i am stuck.
So i setup a jail similar to https://cdn.truenas.com/community/resources/how-to-setup-a-wireguard-vpn-server-in-a-jail.147/.
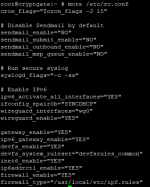
My Jail`s rc.conf:
My /usr/local/etc/ipf.rules (afaik they get never applied):
Jail`s "ipfw show" gives:
Any help is appreciated, thank you!
i am trying to setup a VPN gateway for my local LAN. I don`t want to connect from WAN to my network, i want to use the VPN-Tunnel in the Jail as gateway for my local devices, that don`t have a VPN option. The used Jail release version is 13.1-RELEASE-p5, VNET, BPF, allow_tun are enabled.
So for my understanding i need to setup a working WG tunnel in my Jail (already done!) and have to route the traffic through my jail`s IP from local network nat-ed to the WG IP. And for the routing i have use ipfw rules. A "kill-switch" if no VPN tunnel is active should be configured, too.
I tried several days now and i am stuck.
So i setup a jail similar to https://cdn.truenas.com/community/resources/how-to-setup-a-wireguard-vpn-server-in-a-jail.147/.
- WG in the jail works so far:
- In the jail I can ping the 10.5.0.2 internal WG interface an the 10.5.0.1 of the WG VPN provider server
- A traceroute in the jail shows me, that the jail uses the wg tunnel.
- I can ping the jail from my local network 192.168.8.48.
# $FreeBSD$
#
# This file is read when going to multi-user and its contents piped thru
# ``sysctl'' to adjust kernel values. ``man 5 sysctl.conf'' for details.
#
# Uncomment this to prevent users from seeing information about processes that
# are being run under another UID.
#security.bsd.see_other_uids=0
My Jail`s rc.conf:
cron_flags="$cron_flags -J 15"
# Disable Sendmail by default
sendmail_enable="NO"
sendmail_submit_enable="NO"
sendmail_outbound_enable="NO"
sendmail_msp_queue_enable="NO"
# Run secure syslog
syslogd_flags="-c -ss"
# Enable IPv6
ipv6_activate_all_interfaces="YES"
ifconfig_epair0b="SYNCDHCP"
wireguard_interfaces="wg0"
wireguard_enable="YES"
gateway_enable="YES"
ipv6_gateway_enable="YES"
devfs_enable="YES"
devfs_system_ruleset="devfsrules_common"
inet6_enable="YES"
ip6addrctl_enable="YES"
firewall_enable="YES"
firewall_type="/usr/local/etc/ipf.rules"
My /usr/local/etc/ipf.rules (afaik they get never applied):
ipfw -q add 02000 allow IP from 192.168.8.0/24 to 10.5.0.0/32 keep-state
ipfw -q add 04000 allow IP from 127.0.0.1 to any keep-state
ipfw -q add 05000 allow IP from 10.5.0.0/32 to any keep-state
ipfw -q add 05002 allow IP from any to 10.5.0.0/8 keep-state
Jail`s "ipfw show" gives:
00100 0 0 allow ip from any to any via lo0
00200 0 0 deny ip from any to 127.0.0.0/8
00300 0 0 deny ip from 127.0.0.0/8 to any
00400 0 0 deny ip from any to ::1
00500 0 0 deny ip from ::1 to any
00600 0 0 allow ipv6-icmp from :: to ff02::/16
00700 0 0 allow ipv6-icmp from fe80::/10 to fe80::/10
00800 1 56 allow ipv6-icmp from fe80::/10 to ff02::/16
00900 0 0 allow ipv6-icmp from any to any icmp6types 1
01000 0 0 allow ipv6-icmp from any to any icmp6types 2,135,136
65535 1773 477241 allow ip from any to any
Any help is appreciated, thank you!