Vallevert
Dabbler
- Joined
- Apr 29, 2020
- Messages
- 20
Hi there,
I recently started encrypting the data on my NAS and I have some questions about the security of this system:
1) Does the fact of having encrypted my data make it unreadable for a person who has physical access to the NAS.
For example, if my Mac is stolen, I know that it is not possible for the thief to read the data on it, because the SSD is encrypted and there is no way to access the content without my password.
With TrueNAS (if I understood correctly), you just have to "Reset Root Password" on the console, and the Web GUI is accessible to anyone. Is this correct? Can TrueNAS protect my data from the police force for example?
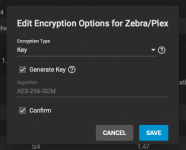
2) I use the "Key" method to encrypt my data [see image]. I have downloaded all my keys on my Mac just in case, to have a backup. Did I do it right? Do you have any suggestions?
3) Personally, for completely random reasons, "Boot-pool" has already died twice. That means I had to reinstall TrueNAS from scratch on my "Boot-pool" disk. Now that my Pools are encrypted, what would happen if "Boot-pool" dies knowing that it contains the encryption keys?
Thank you for your answers and your time.
I recently started encrypting the data on my NAS and I have some questions about the security of this system:
1) Does the fact of having encrypted my data make it unreadable for a person who has physical access to the NAS.
For example, if my Mac is stolen, I know that it is not possible for the thief to read the data on it, because the SSD is encrypted and there is no way to access the content without my password.
With TrueNAS (if I understood correctly), you just have to "Reset Root Password" on the console, and the Web GUI is accessible to anyone. Is this correct? Can TrueNAS protect my data from the police force for example?
2) I use the "Key" method to encrypt my data [see image]. I have downloaded all my keys on my Mac just in case, to have a backup. Did I do it right? Do you have any suggestions?
3) Personally, for completely random reasons, "Boot-pool" has already died twice. That means I had to reinstall TrueNAS from scratch on my "Boot-pool" disk. Now that my Pools are encrypted, what would happen if "Boot-pool" dies knowing that it contains the encryption keys?
Thank you for your answers and your time.