TrueNasForever
Cadet
- Joined
- Aug 7, 2022
- Messages
- 2
Hi,
I switched from core to scale and I don't understand something about the encryption, which consequently changes from Geli to ZFS.
I encrypted my root dataset and switched to passphrase. When I created it I was also prompted to download the key. The password is simple and is just to make sure the disks can't be moved.
Now there is a sub-dataset, which contains more confidential data and also got a much more difficult and secret password. But here I was not asked to save the key.
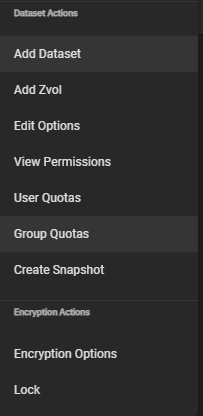
It is also not possible to export the key afterwards, because I cannot find the menu entry "Export Dataset Keys" - mentioned in numerous forum entries - in any dataset.
Now my question:
As far as my knowledge the passphrase is only used to encrypt the data-key. Is this now identical for root and sub dataset and only encrypted with two different passphrases? Or does each have its own data-key that is encrypted with the respective passphrase.
I hope the latter, otherwise I can not use the zfs encryption for my purpose. Just for this last case, where can I export the keys (or just the new key), since I am missing the button.
I didn't find anything on this specific topic, if there is already a forum post, please poke me with my nose on it
Thanks a lot!
I switched from core to scale and I don't understand something about the encryption, which consequently changes from Geli to ZFS.
I encrypted my root dataset and switched to passphrase. When I created it I was also prompted to download the key. The password is simple and is just to make sure the disks can't be moved.
Now there is a sub-dataset, which contains more confidential data and also got a much more difficult and secret password. But here I was not asked to save the key.
It is also not possible to export the key afterwards, because I cannot find the menu entry "Export Dataset Keys" - mentioned in numerous forum entries - in any dataset.
Now my question:
As far as my knowledge the passphrase is only used to encrypt the data-key. Is this now identical for root and sub dataset and only encrypted with two different passphrases? Or does each have its own data-key that is encrypted with the respective passphrase.
I hope the latter, otherwise I can not use the zfs encryption for my purpose. Just for this last case, where can I export the keys (or just the new key), since I am missing the button.
I didn't find anything on this specific topic, if there is already a forum post, please poke me with my nose on it
Thanks a lot!
