Hi,
I was quiet happy with globally setting ACL permissions on my Shares until I needed to manually set a group permissions to read only for a single file.
In the root of one of my shares called "partage" there is a ".share.online" file used by backup sync operations to check if the share is properly mounted.
1- On default inherited settings from the share permissions, here are the ACL permissions of the file:
2- I set the read only attributes on the file for the group "smb_partage"
3- Now, in any client, Android or Windows, any user in the group "smb_partage" can still delete the .share.online file !
4- In windows, I get the warning that permissions are not properly ordered
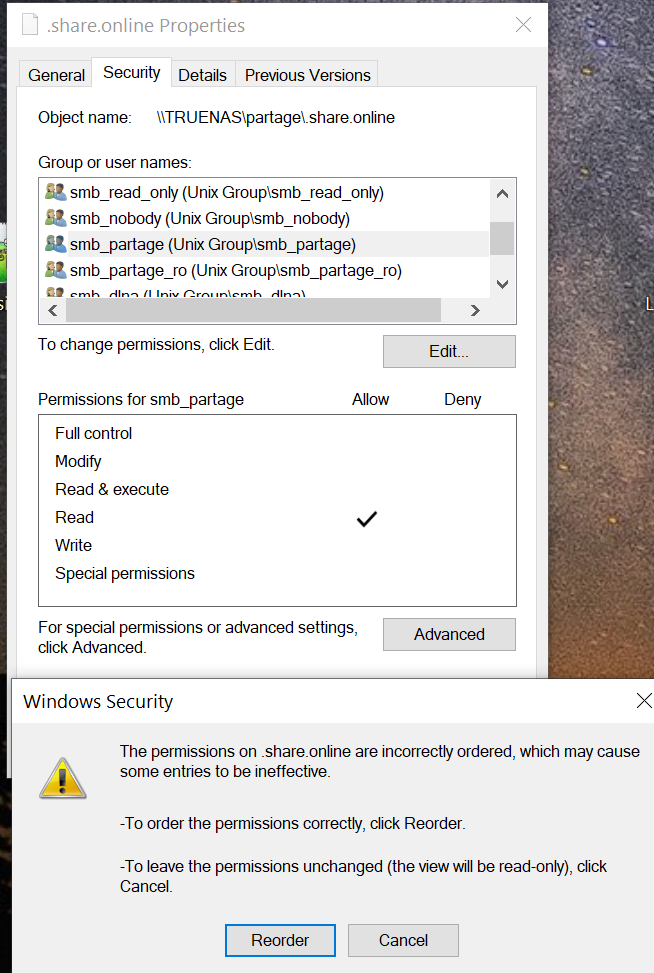
5- If I accept the prompt to order them, the "smb_partage" group is duplicated with the inherited permissions assigned to the new group
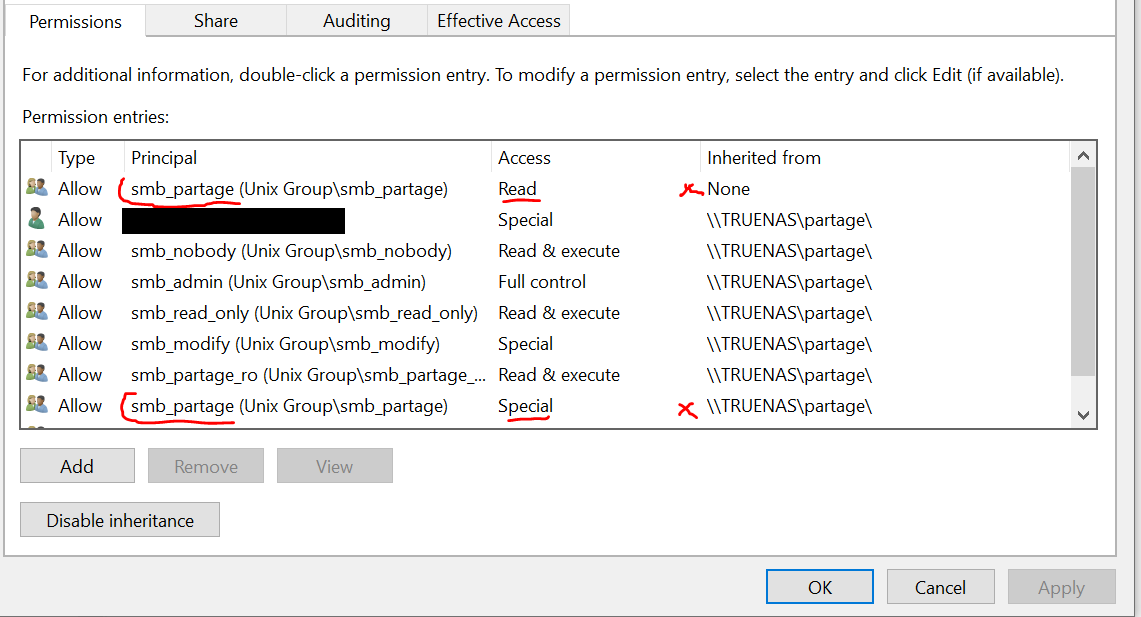
6- I now set the read only attribute on the file: this causes the file to become hidden from listing to any user in the "smb_partage" group
Why applying a different than the inherited ACL to a file causes this issue ? Mainly, it seems that the inherited ACLs always and forcefully apply to created files when using setfacl
Thank you for your help
I was quiet happy with globally setting ACL permissions on my Shares until I needed to manually set a group permissions to read only for a single file.
In the root of one of my shares called "partage" there is a ".share.online" file used by backup sync operations to check if the share is properly mounted.
1- On default inherited settings from the share permissions, here are the ACL permissions of the file:
Code:
getfacl .share.online
# file: .share.online
# owner: someuser
# group: smb_nobody
owner@:rwxpDdaARWc--s:------I:allow
group@:r-x---a-R-c---:------I:allow
group:smb_admin:rwxpDdaARWcCos:------I:allow
group:smb_read_only:r-x---a-R-c---:------I:allow
group:smb_modify:rwxpDdaARWc--s:------I:allow
group:smb_partage_ro:r-x---a-R-c---:------I:allow
group:smb_partage:rwxpDdaARWc--s:------I:allow
group:smb_dlna:r-x---a-R-c---:------I:allow
everyone@:--------------:------I:allow2- I set the read only attributes on the file for the group "smb_partage"
Code:
setfacl -m group:smb_partage:read_set:allow .share.online
getfacl .share.online
# file: .share.online
# owner: someuser
# group: smb_nobody
owner@:rwxpDdaARWc--s:------I:allow
group@:r-x---a-R-c---:------I:allow
group:smb_admin:rwxpDdaARWcCos:------I:allow
group:smb_read_only:r-x---a-R-c---:------I:allow
group:smb_modify:rwxpDdaARWc--s:------I:allow
group:smb_partage_ro:r-x---a-R-c---:------I:allow
group:smb_partage:r-----a-R-c---:-------:allow
group:smb_dlna:r-x---a-R-c---:------I:allow
everyone@:--------------:------I:allow3- Now, in any client, Android or Windows, any user in the group "smb_partage" can still delete the .share.online file !
4- In windows, I get the warning that permissions are not properly ordered
5- If I accept the prompt to order them, the "smb_partage" group is duplicated with the inherited permissions assigned to the new group
Code:
getfacl .share.online
# file: .share.online
# owner: someuser
# group: smb_nobody
group:smb_partage:r-----a-R-c---:-------:allow
owner@:rwxpDdaARWc---:------I:allow
group@:r-x---a-R-c---:------I:allow
group:smb_admin:rwxpDdaARWcCo-:------I:allow
group:smb_read_only:r-x---a-R-c---:------I:allow
group:smb_modify:rwxpDdaARWc---:------I:allow
group:smb_partage_ro:r-x---a-R-c---:------I:allow
group:smb_partage:rwxpDdaARWc---:------I:allow
group:smb_dlna:r-x---a-R-c---:------I:allow6- I now set the read only attribute on the file: this causes the file to become hidden from listing to any user in the "smb_partage" group
Code:
setfacl -m group:smb_partage:r:allow .share.online
# relevant code only:
getfacl .share.online
group:smb_partage:r-------------:-------:allowWhy applying a different than the inherited ACL to a file causes this issue ? Mainly, it seems that the inherited ACLs always and forcefully apply to created files when using setfacl
Thank you for your help
Last edited:
