drgonzo3000
Cadet
- Joined
- Feb 15, 2022
- Messages
- 3
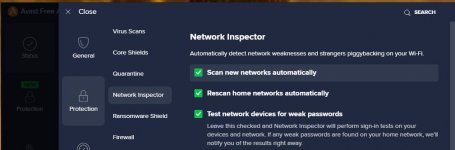
For the past couple weeks now I have been getting security emails about these login attempts on my Freenas server. The server is not exposed to the internet, it is just local network storage. The attempts are coming from a local machine on my network. Looking into the access logs it looks like these login attempts are coming from Avast Antivirus. Has anyone seen anything like this before and is there something that can be done about it?
The IP it's coming from is my Father In-laws work computer. We both work from my house. The computer is virus free and does run Avast paid version. So not too sure what to make of this
Snippet from the Security log output
NGINX Access Logs
The IP it's coming from is my Father In-laws work computer. We both work from my house. The computer is virus free and does run Avast paid version. So not too sure what to make of this
Snippet from the Security log output
Code:
freenas.local login failures: Feb 14 12:51:04 freenas sshd[71399]: Invalid user from 192.168.86.146 Feb 14 12:51:04 freenas sshd[71399]: input_userauth_request: invalid user [preauth] Feb 14 12:51:04 freenas sshd[71399]: Failed none for invalid user from 192.168.86.146 port 54282 ssh2 Feb 14 12:51:04 freenas sshd[71401]: Invalid user Admin from 192.168.86.146 Feb 14 12:51:04 freenas sshd[71401]: input_userauth_request: invalid user Admin [preauth] Feb 14 12:51:04 freenas sshd[71401]: Failed password for invalid user Admin from 192.168.86.146 port 54285 ssh2 Feb 14 12:51:04 freenas sshd[71403]: Failed password for root from 192.168.86.146 port 54288 ssh2 Feb 14 12:51:04 freenas sshd[71405]: Invalid user Administrator from 192.168.86.146 Feb 14 12:51:04 freenas sshd[71405]: input_userauth_request: invalid user Administrator [preauth] Feb 14 12:51:04 freenas sshd[71405]: Failed password for invalid user Administrator from 192.168.86.146 port 54291 ssh2 Feb 14 12:51:04 freenas sshd[71407]: Invalid user admin from 192.168.86.146 Feb 14 12:51:04 freenas sshd[71407]: input_userauth_request: invalid user admin [preauth] Feb 14 12:51:04 freenas sshd[71407]: Failed password for invalid user admin from 192.168.86.146 port 54294 ssh2 Feb 14 12:51:04 freenas sshd[71409]: Invalid user admin from 192.168.86.146 Feb 14 12:51:04 freenas sshd[71409]: input_userauth_request: invalid user admin [preauth] Feb 14 12:51:04 freenas sshd[71409]: Failed password for invalid user admin from 192.168.86.146 port 54297 ssh2 Feb 14 12:51:04 freenas sshd[71411]: Invalid user admin from 192.168.86.146 Feb 14 12:51:04 freenas sshd[71411]: input_userauth_request: invalid user admin [preauth] Feb 14 12:51:04 freenas sshd[71411]: Failed none for invalid user admin from 192.168.86.146 port 54302 ssh2 Feb 14 12:51:04 freenas sshd[71413]: Invalid user user from 192.168.86.146
NGINX Access Logs
Code:
192.168.86.146 - - [14/Feb/2022:12:50:55 -0500] "GET / HTTP/1.1" 302 5 "-" "Avast Antivirus" 192.168.86.146 - - [14/Feb/2022:12:50:55 -0500] "GET /account/login/?next=/ HTTP/1.1" 200 5935 "-" "Avast Antivirus" 192.168.86.146 - - [14/Feb/2022:12:50:55 -0500] "GET /HNAP1/ HTTP/1.1" 302 5 "-" "Avast Antivirus" 192.168.86.146 - - [14/Feb/2022:12:50:55 -0500] "GET / HTTP/1.1" 302 5 "-" "Avast Antivirus" 192.168.86.146 - - [14/Feb/2022:12:50:55 -0500] "GET /account/login/?next=/ HTTP/1.1" 200 5935 "-" "Avast Antivirus" 192.168.86.146 - - [14/Feb/2022:12:51:07 -0500] "POST /cgi-bin/mainfunction.cgi HTTP/1.1" 302 5 "-" "Avast Antivirus" 192.168.86.146 - - [14/Feb/2022:12:51:07 -0500] "GET / HTTP/1.1" 302 5 "-" "Avast Antivirus" 192.168.86.146 - - [14/Feb/2022:12:51:07 -0500] "GET /account/login/?next=/ HTTP/1.1" 200 5935 "-" "Avast Antivirus"