SSH Service Screen
3 minute read.
The System > Services > SSH screen allows you to set up SSH service on TrueNAS.
Click edit to open the Services > SSH configuration screen.
Allowing external connections to TrueNAS is a security vulnerability! Do not enable SSH unless you require external connections. See Security Recommendations for more security considerations when using SSH.
You must also configure SSH backup credentials to allow SSH access. See SSH Screens for more information.
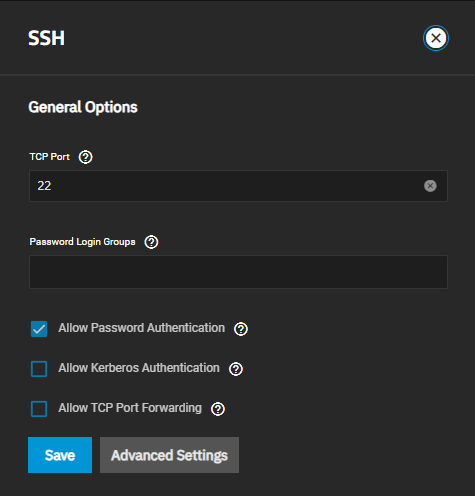
The Basic Settings options display by default when you edit the SSH service.
| Setting | Description |
|---|---|
| TCP Port | Enter the port number for SSH connection requests. |
| Password Login Groups | List of TrueNAS account groups allowed to use a password for logging in to the system with SSH. Click in the field to see a list of current account groups. Begin typing in the field to filter the groups list. Left click a list item to add it to the field. Click the for an entry to remove it from the field. |
| Allow Password Authentication | Select to enable and allow using a password to authenticate the SSH login. If disabled (not selected), authentication changes to require SSH keys for all users. This requires additional setup for both the SSH client and server. Warning: when directory services are enabled, this setting grants access to all users the directory service imported. |
| Allow Kerberos Authentication | Select to allow Kerberos authentication. Ensure valid entries exist in Directory Services > Kerberos Realms and Directory Services > Kerberos Keytabs and the system can communicate with the Kerberos domain controller before enabling this option. |
| Allow TCP Port Forwarding | Select to allow users to bypass firewall restrictions using SSH port forwarding. For best security, leave disabled and deny shell access to users. |
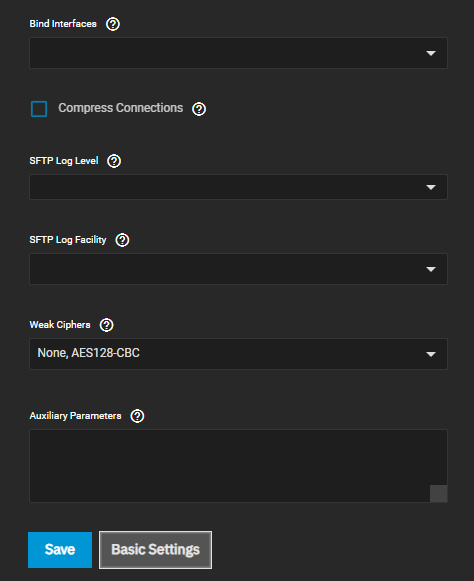
Advanced Settings include the General Options settings. Advanced settings specify bind interfaces, SFTP settings, ciphers and any additional parameters you want to use.
| Setting | Description |
|---|---|
| Bind Interfaces | Select the network interface configured on your system for SSH to listen on from the dropdown list. Leave all options unselected for SSH to listen on all interfaces. |
| Compress Connections | Select to attempt to reduce latency over slow networks. |
| SFTP Log Level | Select the syslog(3) level of the SFTP server from the dropdown list. Options are Quiet, Fatal, Error, Info, Verbose, Debug, Debug2 or Debug3. |
| SFTP Log Facility | Select the syslog(3) facility of the SFTP server option from the dropdown list. Options are Daemon, User, Auth and Local 0 through Local7. |
| Weak Ciphers | Select a cipher from the dropdown list. Options are None or AES128-CBC. To allow more ciphers for sshd(8) in addition to the defaults in sshd_config(5). Use None to allow unencrypted SSH connections. Use AES128-CBC to allow the 128-bit Advanced Encryption Standard. WARNING: These ciphers are security vulnerabilities. Only allow them in a secure network environment. |
| Auxiliary Parameters | Enter any sshd_config(5) options not covered in this screen. Enter one option per line. Parameters added are case-sensitive. |
Auxiliary parameters are an unsupported configuration. Parameters entered here are not validated and can cause undefined system behavior, including data corruption or data loss.