Block (iSCSI) Share Target Screens
16 minute read.
The Sharing screen opens after you click Shares on the main navigation panel.
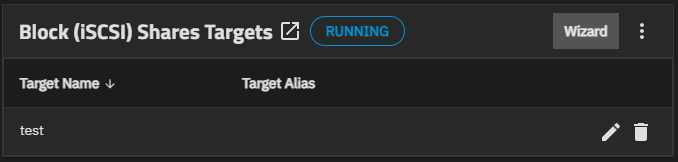
The Block (iSCSI) Shares Targets widget header shows the status of the iSCSI service, the Wizard button, and the icon button. Wizard opens the Wizard iSCSI wizard on the Target screen. See Target Screens below.
The shows two options: a toggle for Turn On Service/Turn Off Service and Config Service. Config Service opens the *iSCSI Global Configuration screen.
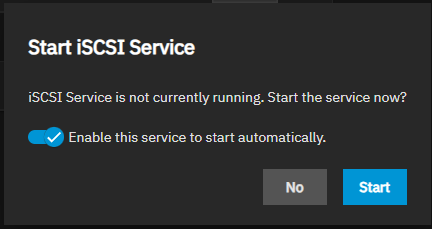
The Start iSCSI Service dialog shows after adding the first share. It includes an Enable this service to start automatically toggle and two buttons: Start and No. Start starts the service and changes the status on the iSCSI widget toolbar from STOPPED (in red) to RUNNING (in blue).
Click anywhere on Block (iSCSI) Shares Targets header to open the Sharing > iSCSI > Targets screen.
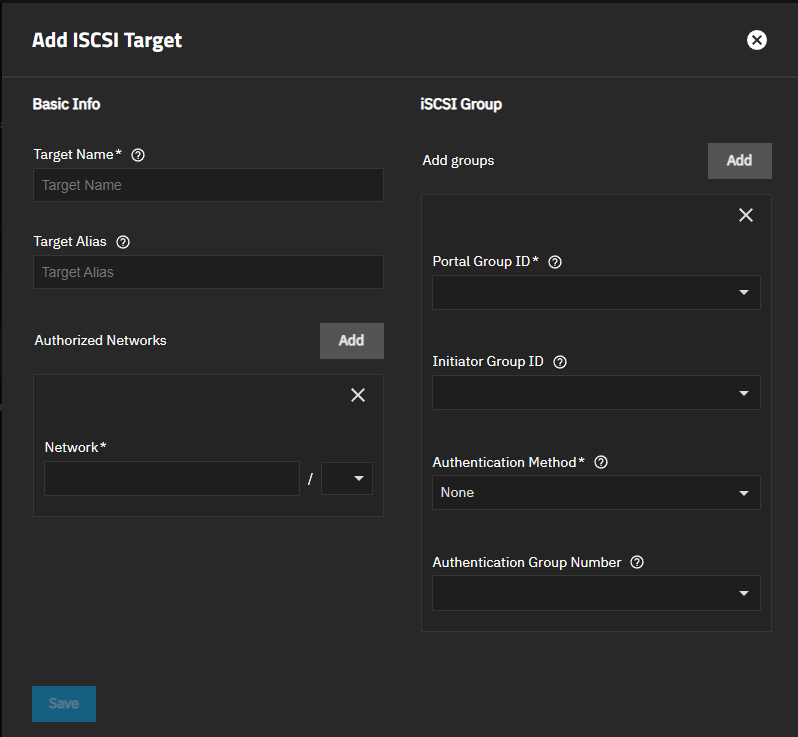
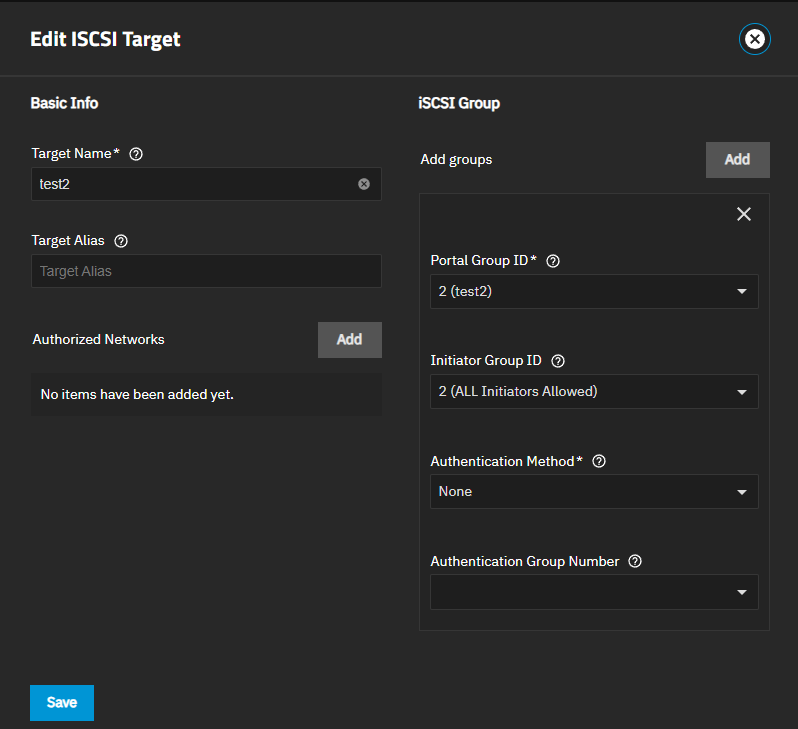
Add opens the Add ISCSI Target screen. Edit opens the Edit iSCSI Target screen.
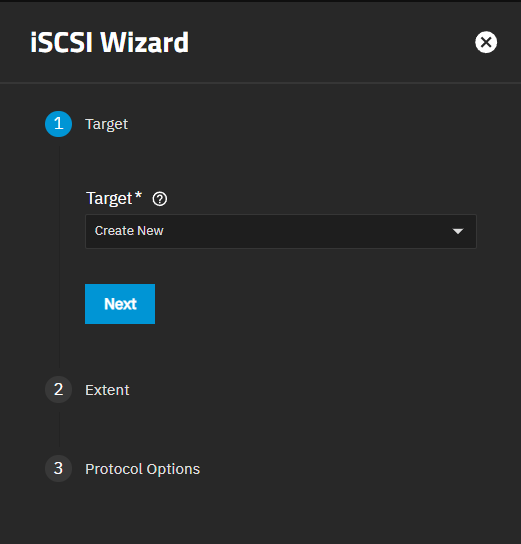
The Wizard button opens the iSCSI wizard on the Targets screen. The wizard has three screens:
- Target
- Extent
- Protocol Options
The individual iSCSI screens are accessed by clicking on the iSCSI widget header. The Targets screen opens by default. For more information on iSCSI screens and settings, see Shares iSCSI Screens below.
Next advances to the next wizard screen. Back shows the previous wizard screen. Save creates the iSCSI share.
The iSCSI Wizard opens showing the Target screen.
The Target dropdown shows the default Create New. Selecting Create New creates a share, or selecting an existing target from the dropdown list allows you to edit it.
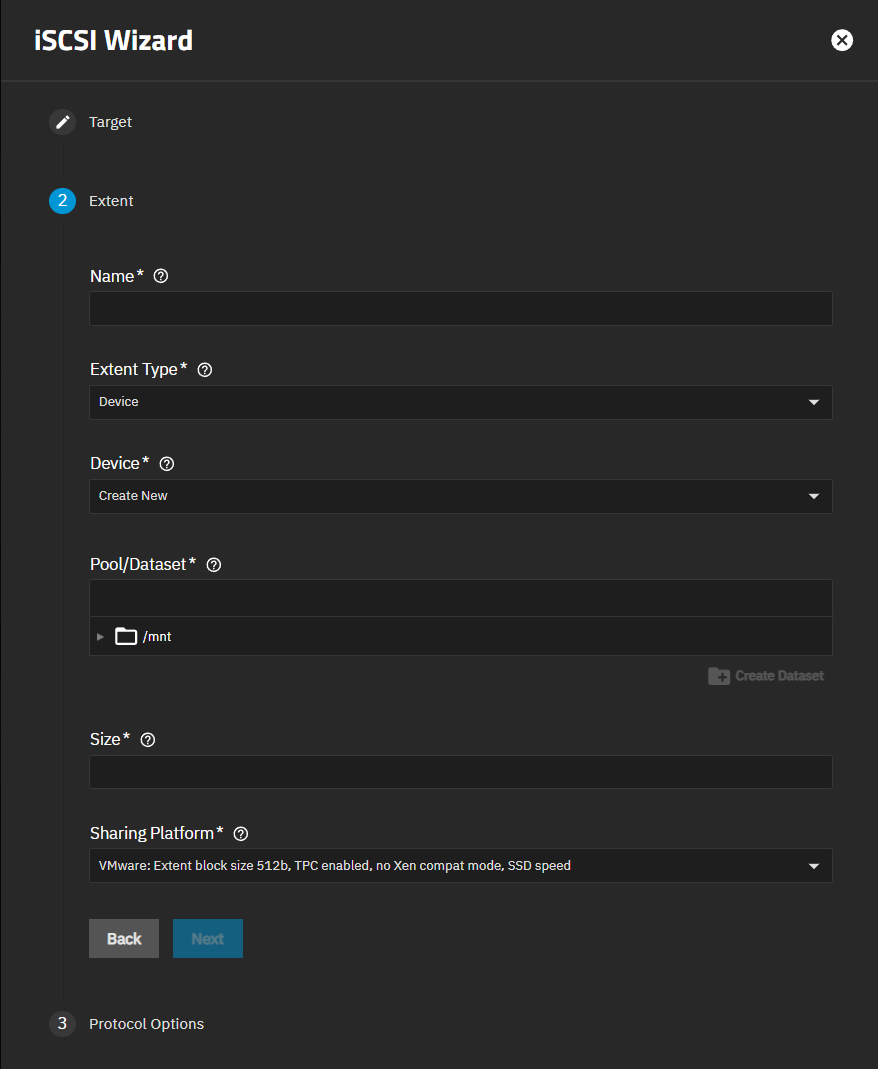
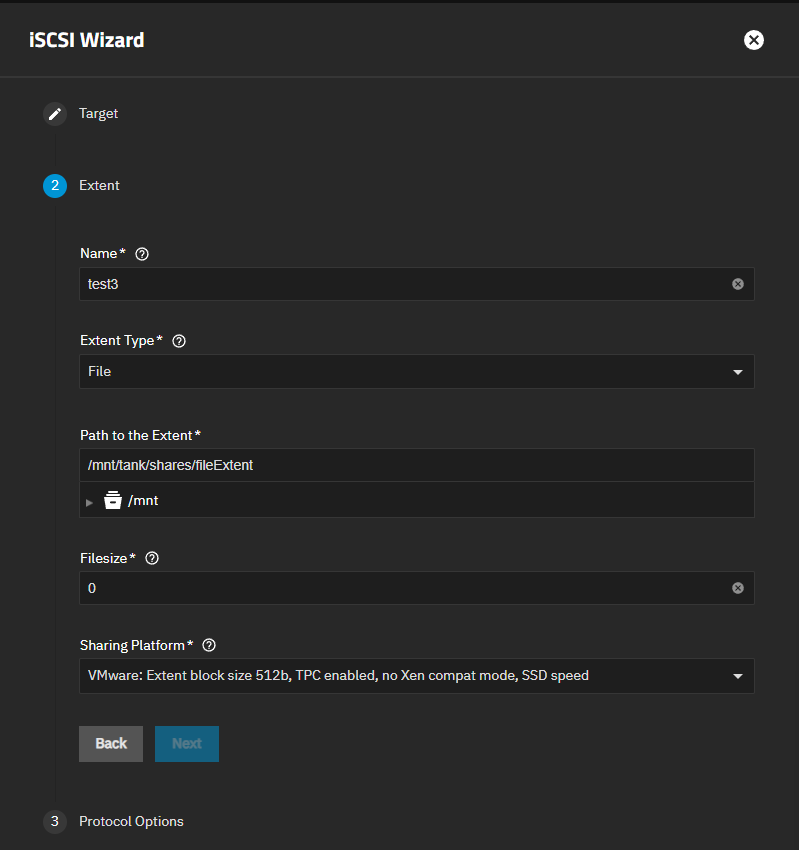
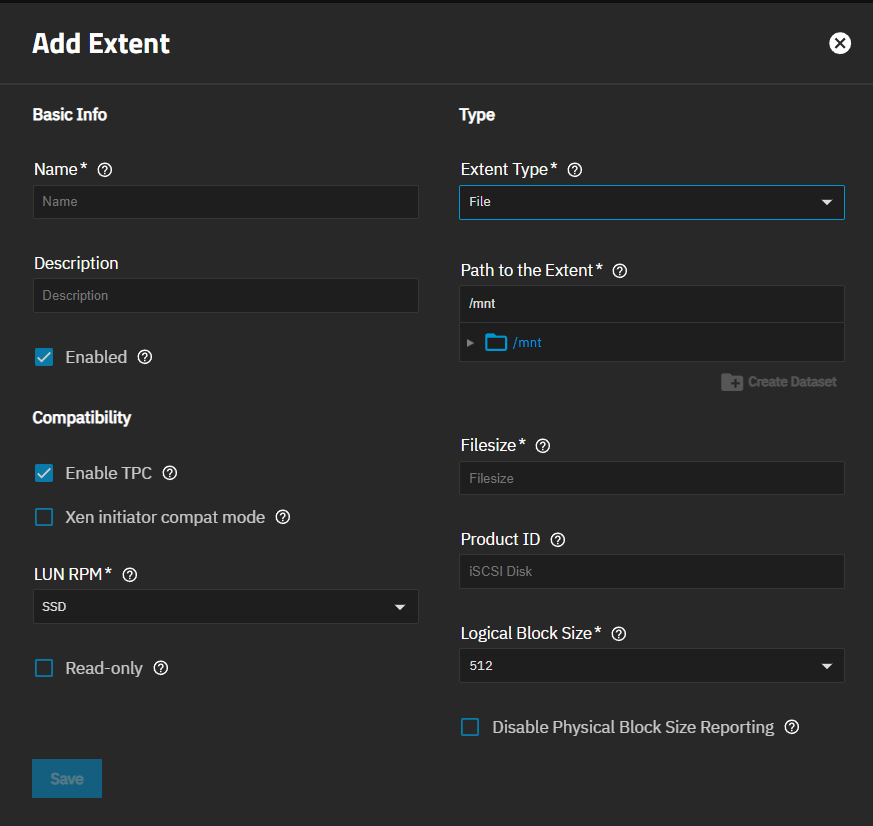
The iSCSI wizard Extent screen shows settings to name the share, set the type of extent devices, and the sharing platform for the device.
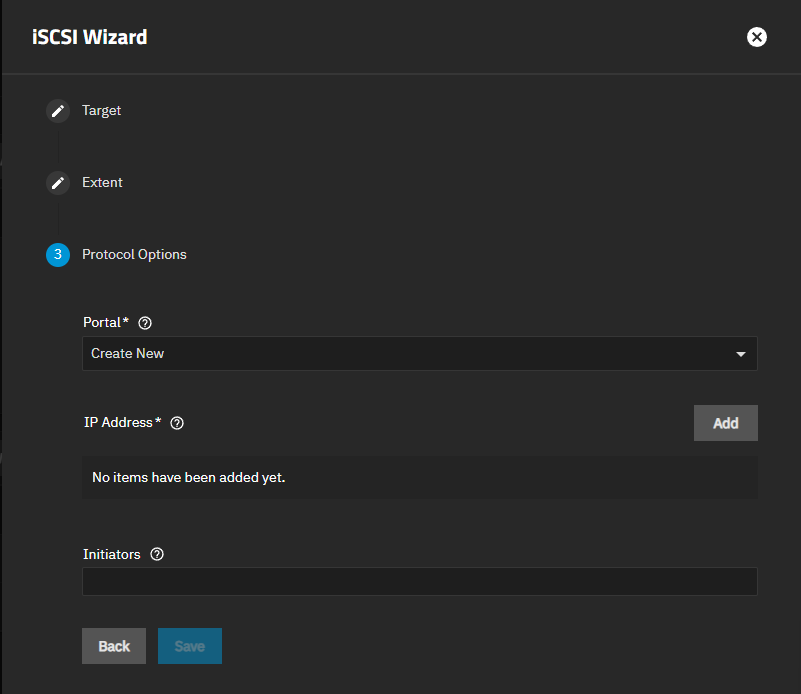
The iSCSI wizard Protocol Options screen shows settings to add a portal and initiators. If a portal does not exist, create one by selecting Create New.
Clicking on the iSCSI widget header opens the iSCSI share screens.
Global Target Configuration opens the iSCSI service configuration screen.
Wizard opens the iSCSI wizard configuration screens.
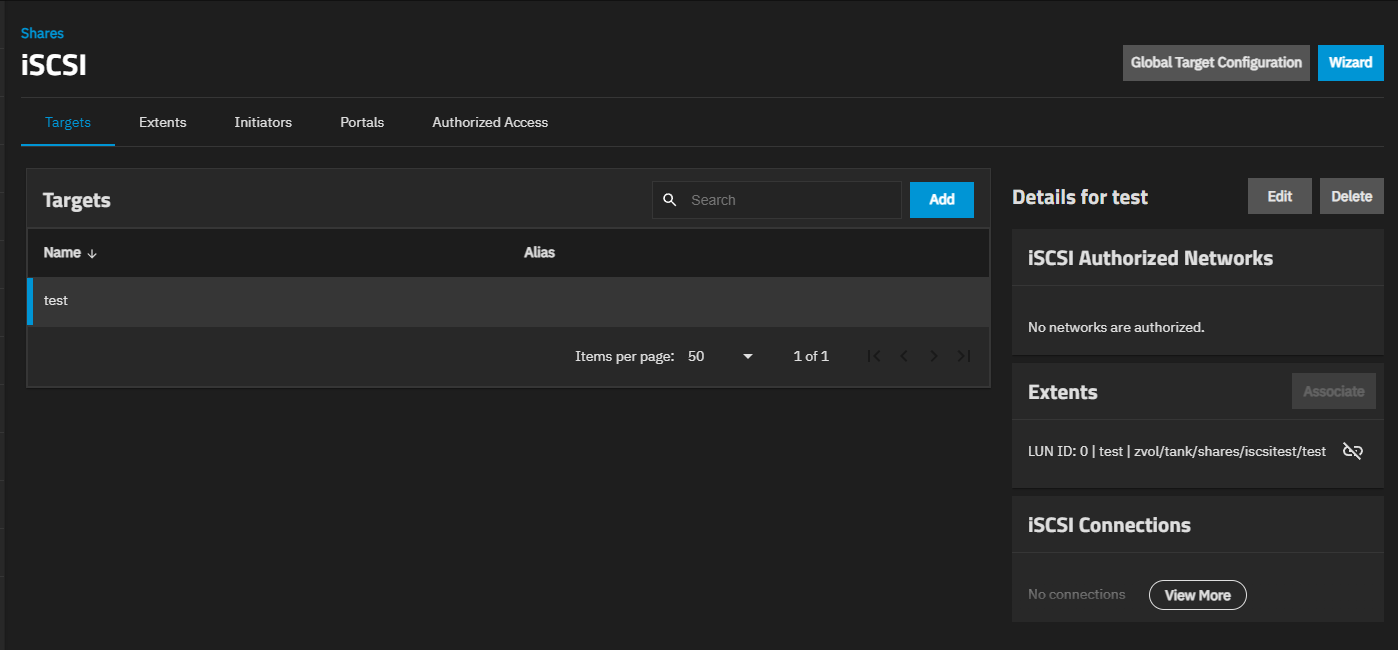
The iSCSI shares screen opens showing Targets by default.
Five tabs show for each of the following screens: Targets, Extents, Initiators, Portals, and Authorized Access. Each shows what is configured on the system, and provides access to the add and edit configuration screens for each functional area.
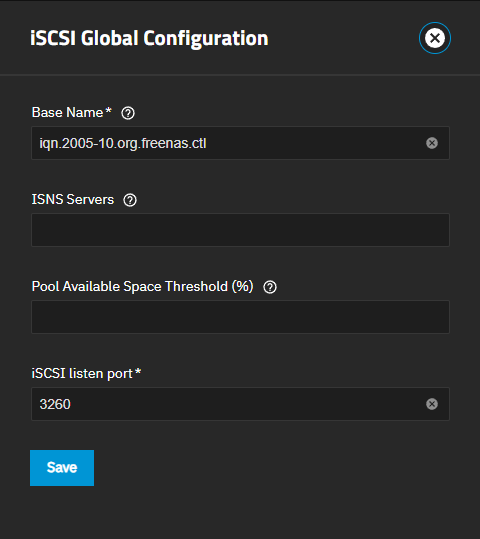
The iSCSI Global Configuration screen opens when you click Edit on the iSCSI Service row of the System > Services screen, and after clicking the Global Target Configuration button at the top of all iSCSI share screens.
The iSCSI Targets screen shows a list of targets configured in the system and provides access to the add and edit configuration screens. Select a target to see details about that item.
Add and Edit open the configuration screen for the selected target. Delete opens a dialog with delete options.
The screen shows three widgets on the right side of the screen for the selected target: iSCSI Authorized Networks, Extents, and iSCSI Connections.
iSCSI Authorized Networks shows a list of authorized networks configured when you create the target. Edit the target to add networks to an existing target.
Extents shows a list of LUNs, and includes two options: Associate button and a Remove Extent Association icon.
iSCSI Connections shows a list of the connections configured on the system.
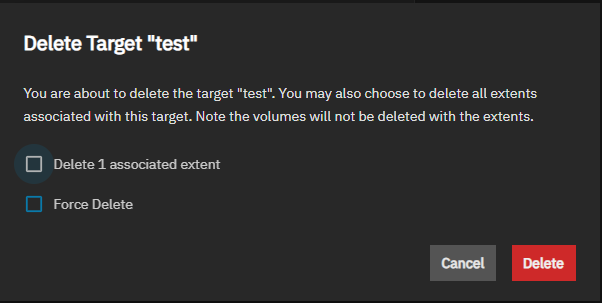
Delete opens a confiration dialog with two options: Delete 1 associated extent and Force Delete. Select the options to include in the delete operation.
Delete 1 associated extent shows the number of associated extend for the selected target.
Force Delete deletes the target even if the share is still in use.
Cancel closes the dialog without deleting. Delete deletes the target but does not delete the iSCSI volumes associated with the extents.
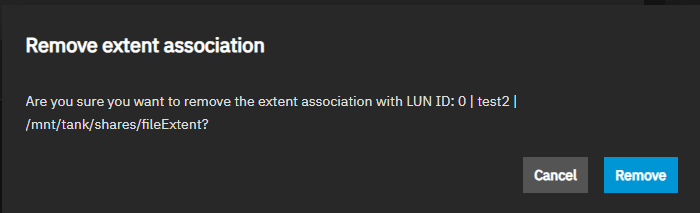
The Remove Extent Association icon opens the Remove extent association dialog that shows the LUN link association and two buttons: Cancel and Remove. Removing the association activates the Associate button on the widget.
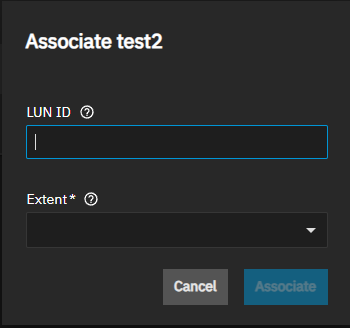
The Associate button is inactive when the extent is associated with a LUN. Removing the association activates the button. Clicking the button opens the Associate target dialog.
Enter a LUN ID between 0 and 1023 into LUN ID. SCALE requires at least one LUN 0. Some initiators expect a value between 0 and 256. Leaving this field blank automatically assigns the next available ID.
Select the target on the Extent dropdown list.
The Add Target and Edit Target screens show the same configuration settings.
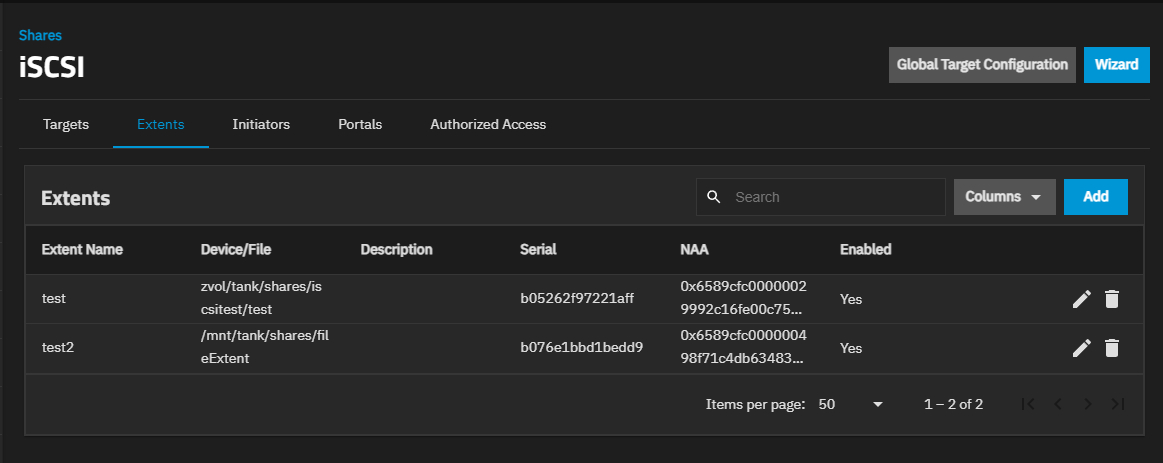
The Extents screen shows a table listing extents configured on the system. Extents are shared storage units.
Add and Edit open the configuration screen for the selected target. Delete opens a dialog with delete options.
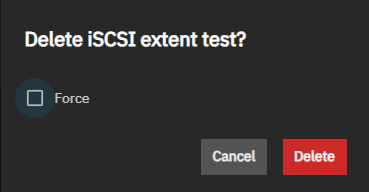
The Delete iSCSI Extent name deletes the specified extend. The name of the extent shows in the dialog title.
Force allows deleting the extend even if the share is active.
Delete deletes the extent and closes the dialog. Cancel closes the dialog without deleting the extent.
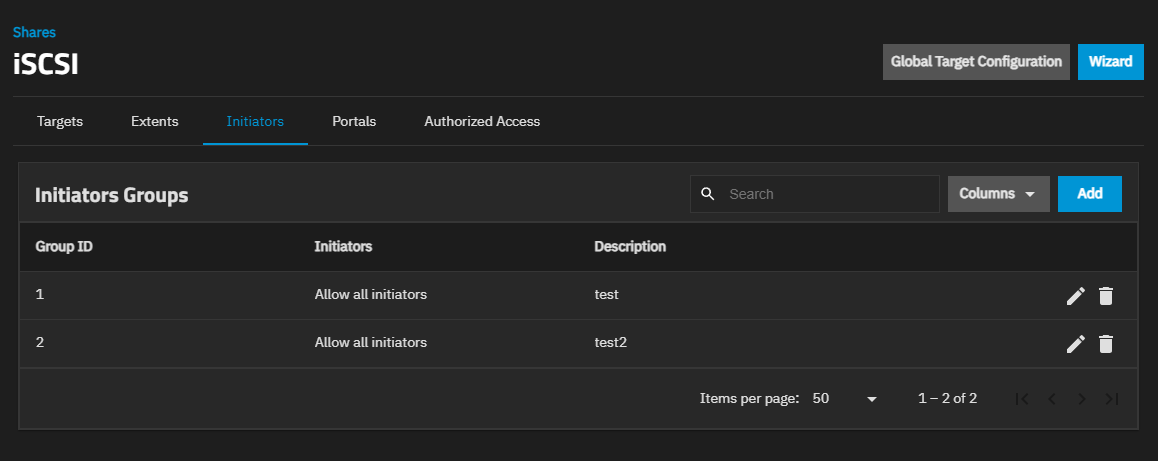
The Initiators Groups screen shows after clicking the Initiator tab. The table lists initiator groups configured on the system.
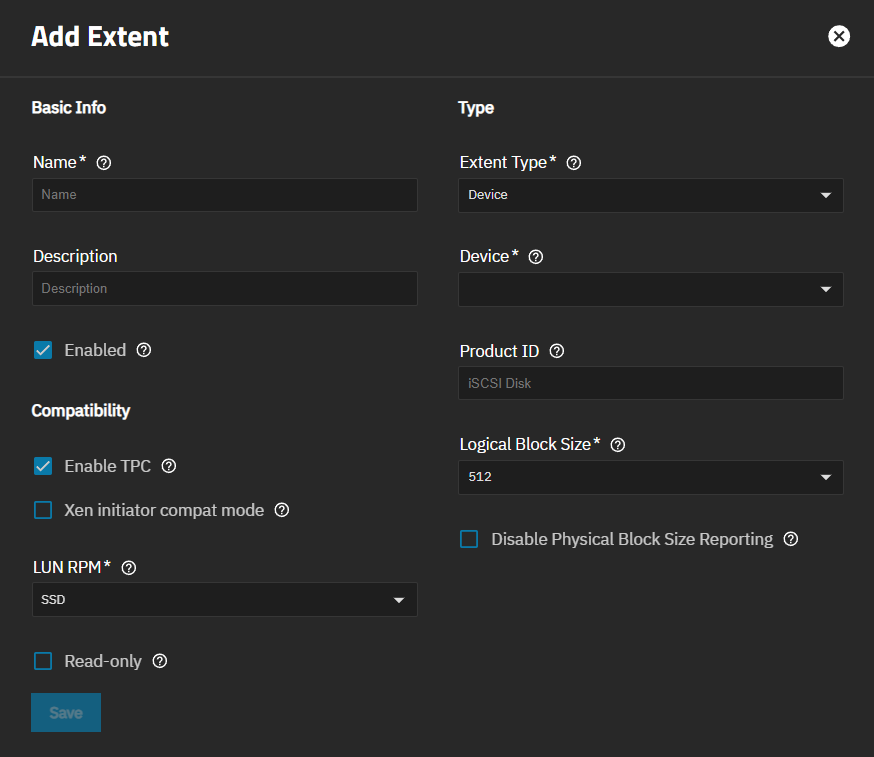
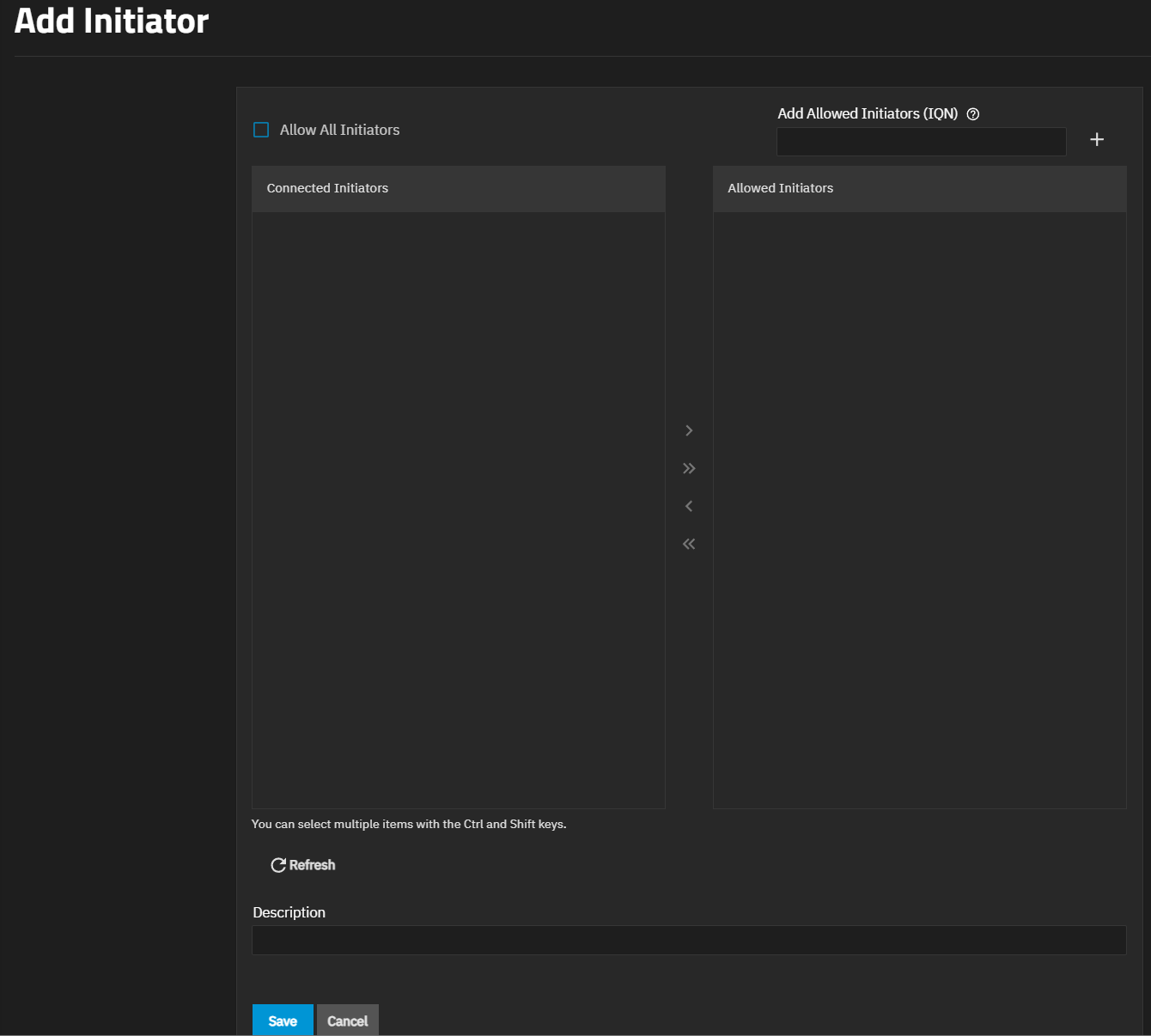
Add opens the Add Initiator screen. Edit opens a version of the Add Initiator screen with only two fields. Delete opens a dialog to delete an initiator group.
Add opens the Add Initiator screen showing the settings to create new authorized access client groups or edit existing ones in the list.
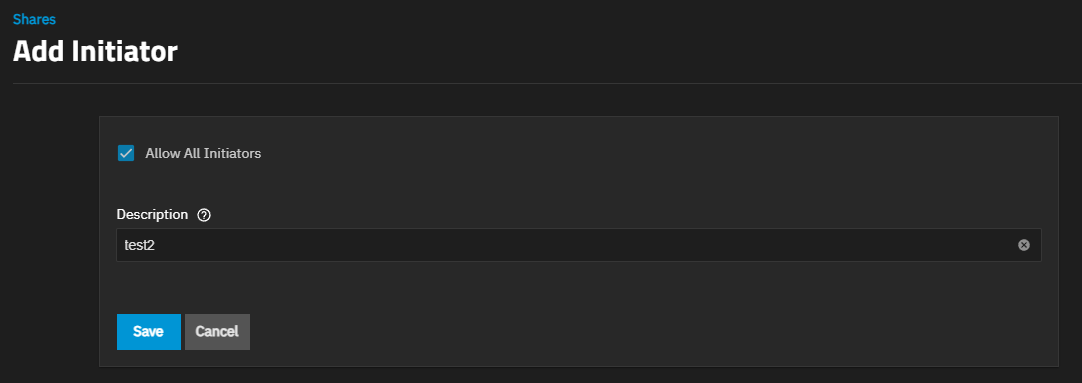
Edit opens the Add Initiator edit screen showing two options: Allow All Initiators and Description. Save saves changes and closes the screen. Cancel closes the screen without saving changes.
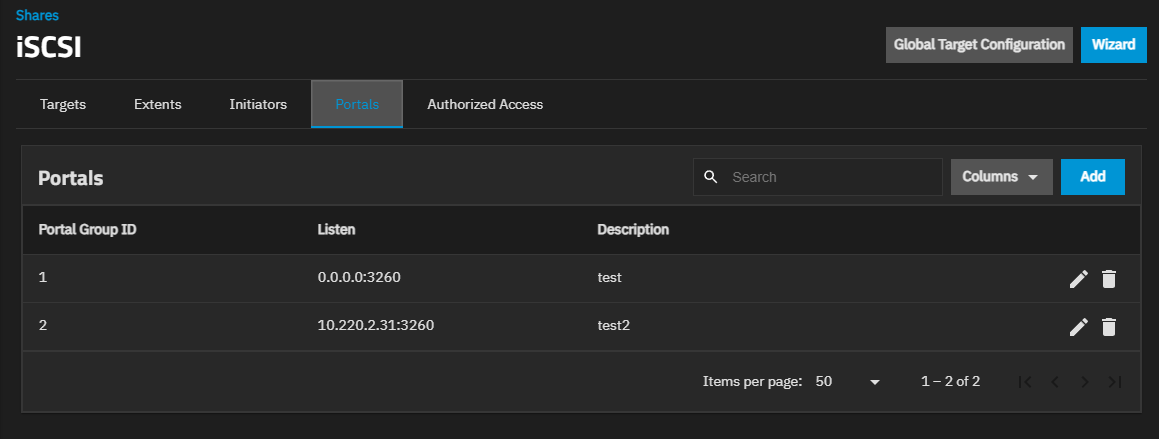
The configuration tabs Portals screen displays a list of portal ID groups on the TrueNAS system.
Delete opens the Delete dialog for the selected portal ID. Click Confirm and then Delete to delete the selected portal.
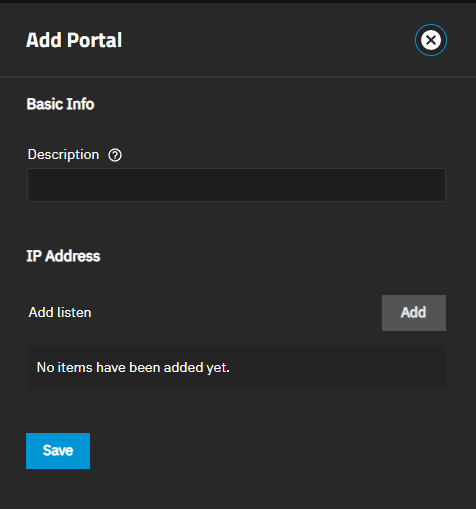
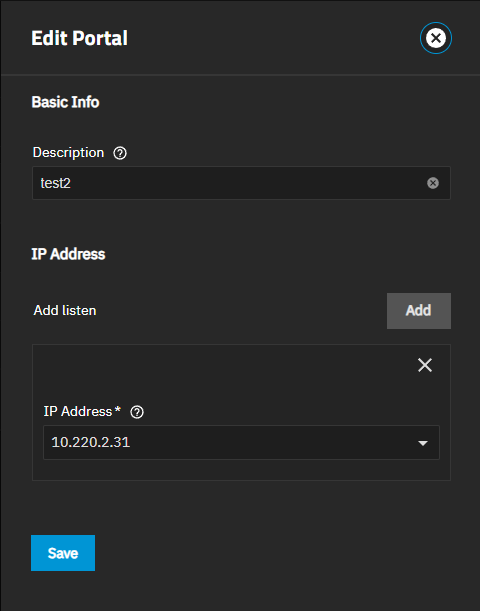
Add opens the Add Portal screen. Edit opens the Edit Portal screen. Both screens have the same setting options.
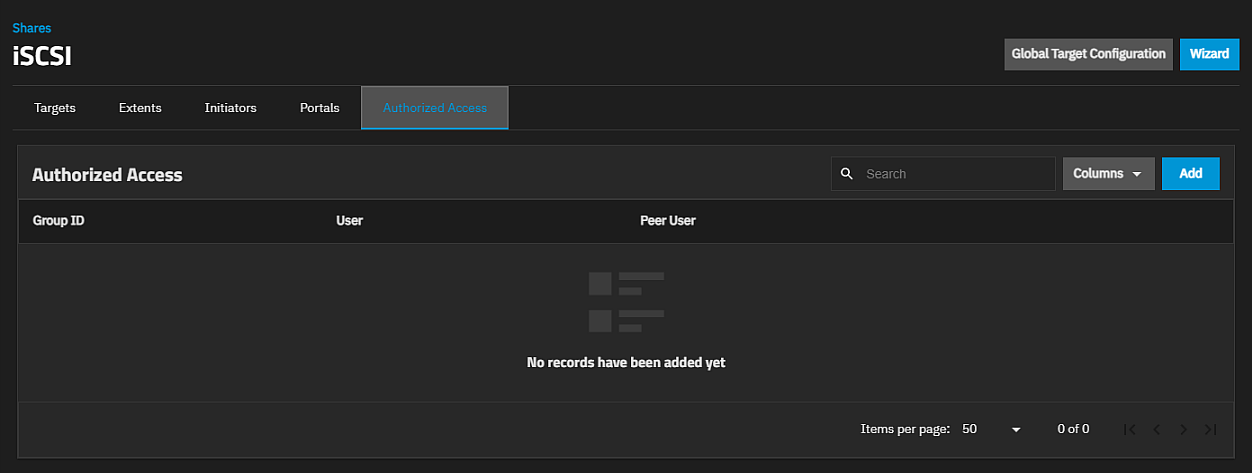
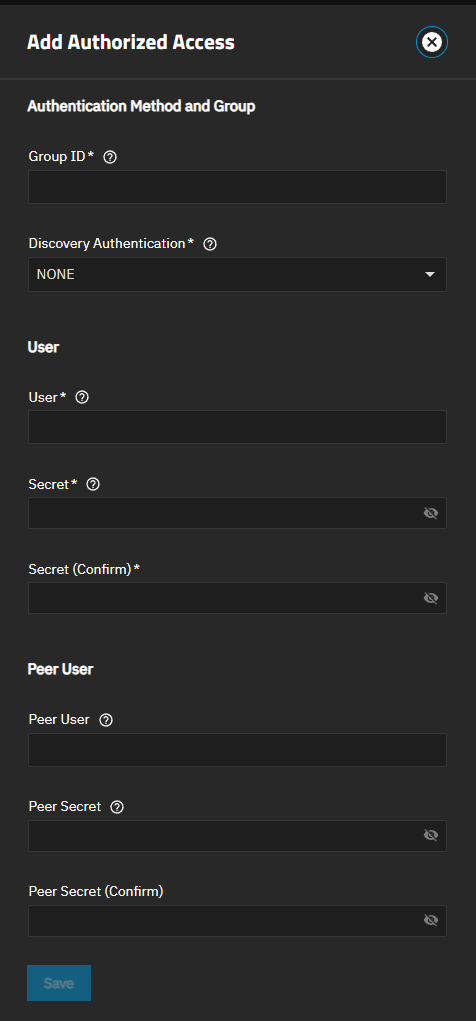
The Authorized Access screen displays settings to create new authorized access networks or edit existing ones in the list.
If you have not set up authorized access yet, the No Authorized Access screen displays with the Add Authorized Access button in the center of the screen. Add Authorized Access or Add at the top of the screen opens the Add Authorized Access screen.
After adding authorized access to the system, the Authorized Access screen displays a list of users. Delete opens the Delete dialog for the selected portal ID. Confirm enables the delete option. Delete deletes the selected portal and closes the dialog.
Add opens the Add Authorized Access screen.
Edit opens the Edit Authorized Access screen. Delete opens a dialog to delete the authorized access for the selected user.
The Add and Edit screens display the same settings. Both screens have the same setting options.