Directory Services Screens
2 minute read.
The Directory Services screen and widgets provide access to TrueNAS settings to set up access to directory services and advanced authentication systems deployed in user environments.
TrueNAS does not configure Active Directory domain controllers or LDAP directory servers, nor does it configure Kerberos authentication servers or ID mapping systems.
Refer to documentation for these services and systems for information on how to configure each to suit your use case.
The Directory Services screen configuration options set up access to directory servers through domain and account settings, and can set up ID mapping or Kerberos authentication and authorization services.
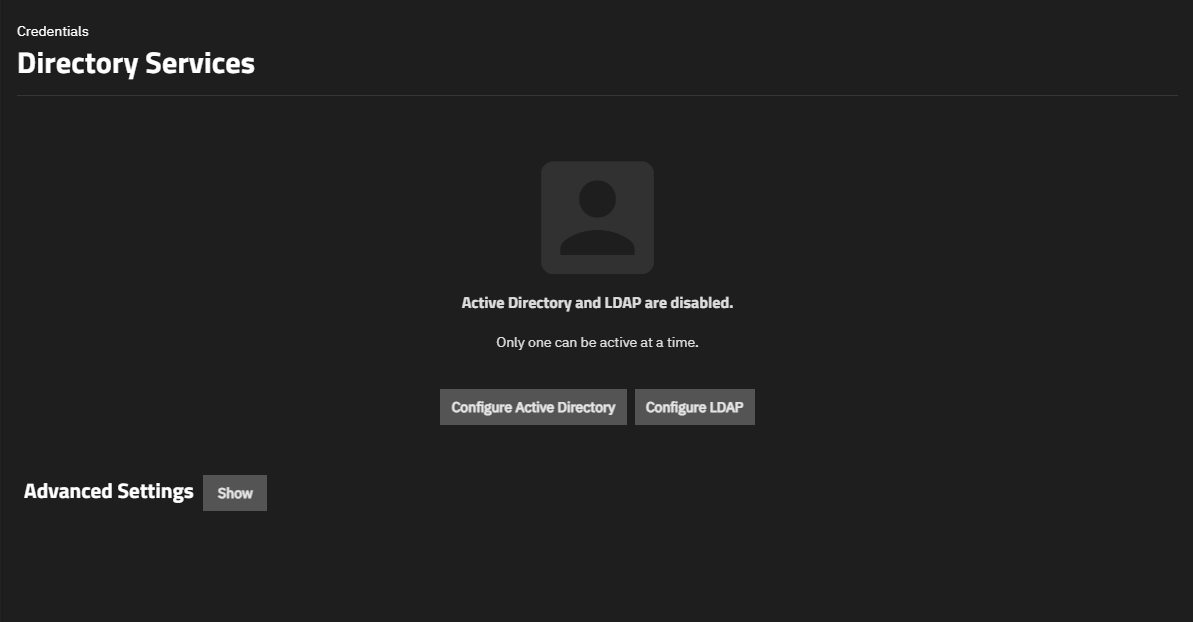
The screen shows the status of directory services when a service is not configured or when it is configured but disabled.
The main option displays:
Configure Directory Services opens the Directory Services Configuration form where you can set up Active Directory, IPA, or LDAP connections.
Advanced Settings opens a warning dialog before showing configuration options for Kerberos.
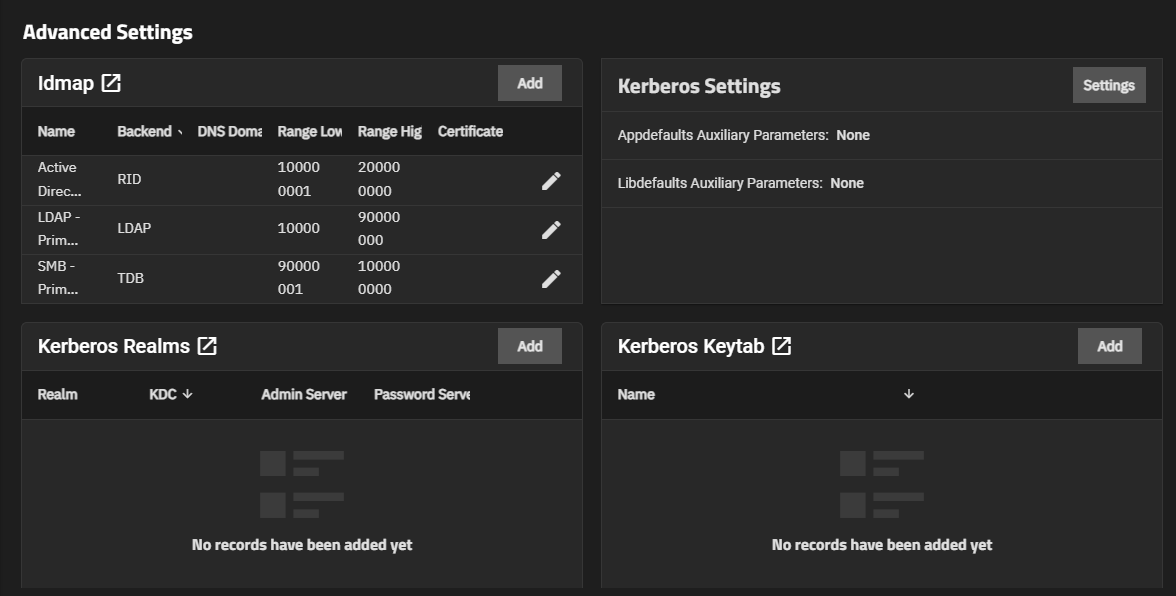
After configuring Active Directory, IPA, or LDAP, the Directory Services screen includes the widget for the configured service, and adds the Show button to the right of Advanced Settings. Show opens the warning dialog stating incorrectly configuring advanced settings is dangerous.
Advanced Settings shows a warning dialog stating incorrectly configuring advanced settings is dangerous. Continue closes the dialog and shows the Kerberos Settings, Kerberos Realms, and Kerberos Keytabs configuration widgets.