Certificates Screens
10 minute read.
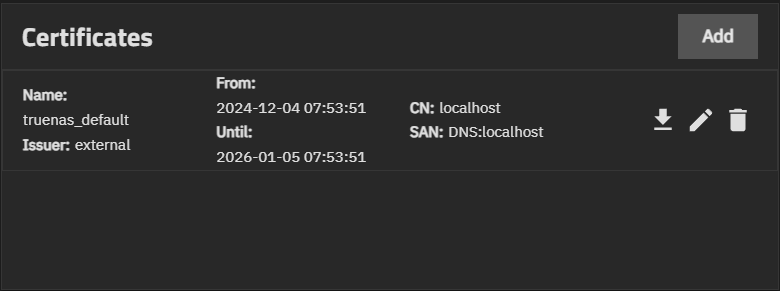
The Certificates widget on the Credentials > Certificates screen displays certificates added to TrueNAS and allows you to add new certificates, or download, delete, or edit the name of an existing certificate. Each TrueNAS has an internal, self-signed certificate that enables encrypted access to the web interface.
The
deletes the certificate from your server.
Each certificate listed on the widget is a link that opens the Edit Certificate screen.
Add opens the Add Certificate wizard.
The Add Certificate wizard screens guide users through configuring a new certificate on TrueNAS. The wizard has five different configuration screens, one for each step in the certificate configuration process:
Many of the settings in the Add Certificate wizard are the same as those in the Add CA and Add Certificate Signing Request wizards.Before you create a new certificate, configure a new CA if you do not already have one on your system. Creating an internal certificate requires a CA to exist on the system.
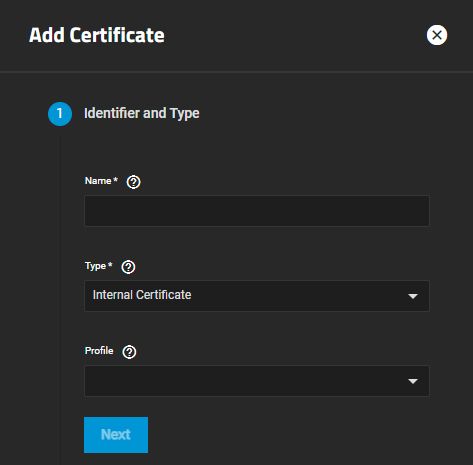
The Identifier and Type options specify the certificate name and choose whether to use it for internal or local systems or import an existing certificate.
Users can also select a predefined certificate extension from the Profiles dropdown list.
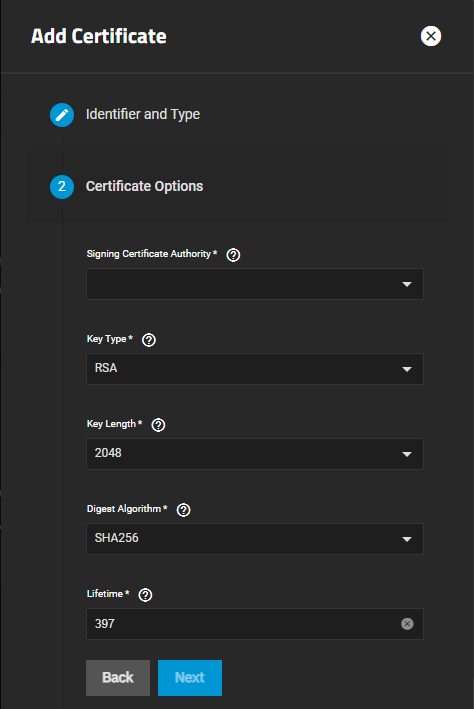
Certificate Options settings choose the signing certificate authority (CSR), the type of private key type to use (as well as the number of bits in the key used by the cryptographic algorithm), the cryptographic algorithm the certificate uses, and how many days the certificate authority lasts.
The Certificate Options settings change based on the selection in Type on the Identifier and Type screen.
The Key Type selection changes fields displayed. RSA is the default setting in Key Type. The Signing Certificate Authority field requires you to have a CA already configured on your system. If you do not have a Certificate Authority (CA) configured on your system, exit the Add Certificate wizard and add the required CA.
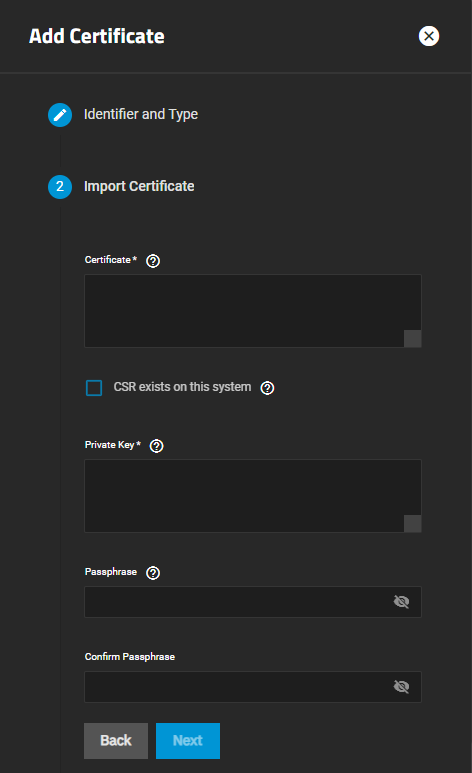
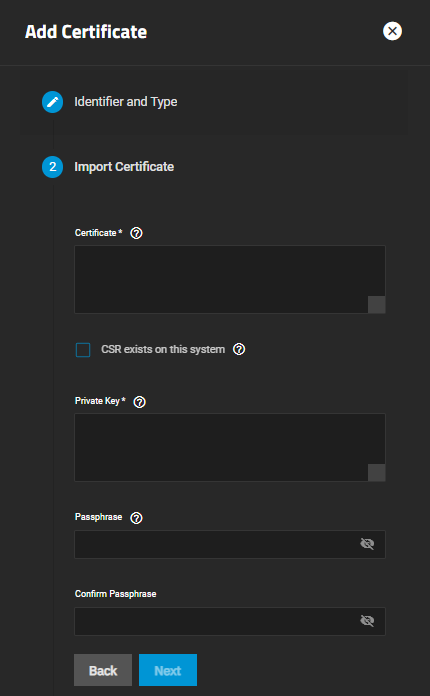
Setting Type on the Identifier and Type screen to Import Certificate changes the options displayed on the Certificate Options configuration screen.
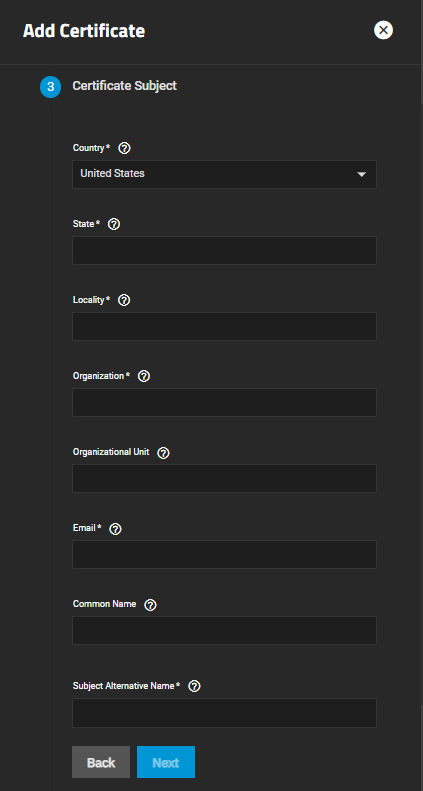
The Certificate Subject step lets users define the location, name, and email of the organization using the certificate.
Users can also enter the system fully-qualified hostname (FQDN) and any additional domains for multi-domain support.
The Certificate Subject screen does not display when Type on Internal Certificate is set to Import Certificate.
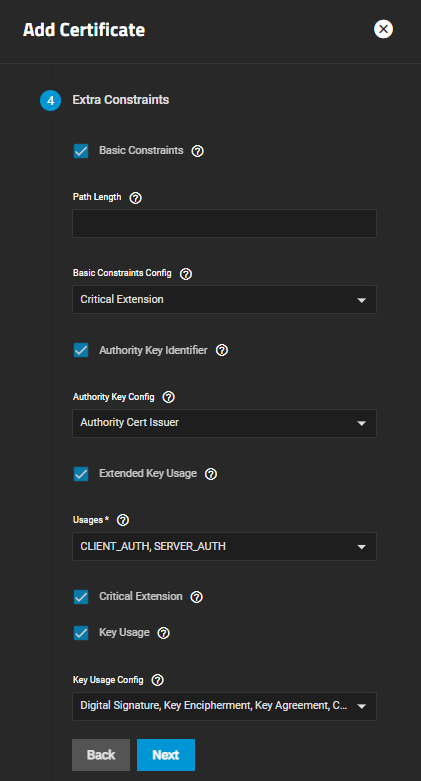
The Extra Constraints step contains certificate extension options.
- Basic Constraints limits the path length for a certificate chain.
- Authority Key Identifier provides a means of identifying the public key corresponding to the private key used to sign a certificate.
- Key Usage defines the purpose of the public key contained in a certificate.
- Extended Key Usage further refines key usage extensions.
The Extra Constraints settings change based on the selection in Type on the Identifier and Type screen.
After selecting Basic Constraints, Authority Key Identifier, Extended Key Usage, or Key Usage, each displays more settings that the option needs.
When Type on Identifier and Type is set to Import Certificate the Import Certificate options screen displays.
The final step screen is the Confirm Options that displays the certificate Type, Key Type, Key Length, Digest Algorithm, Lifetime, Country, and any configured Usages.
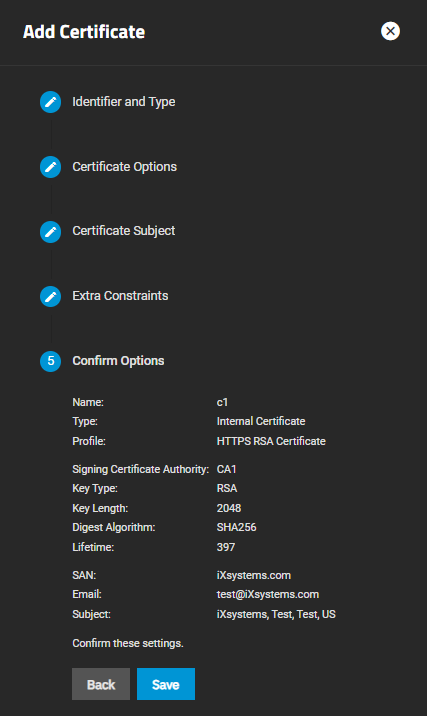
Save adds the certificate to TrueNAS. Back returns to previous screens to make changes before you save. Next advances to the next screen in the sequence to return to Confirm Options.
The certificate listed on the Certificates widget is a link that opens the Edit Certificate screen.
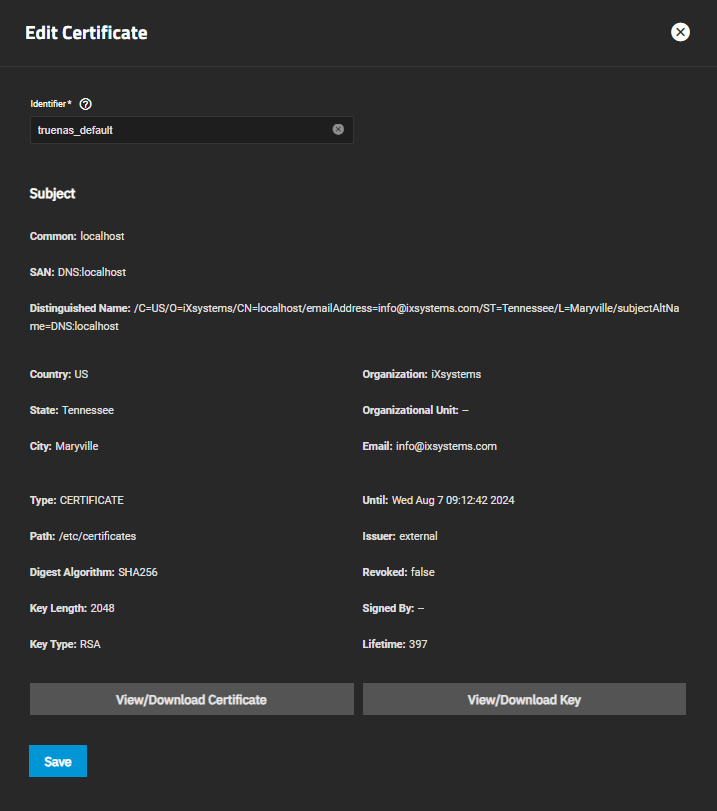
The Edit Certificate screen displays the fixed Subject settings, the type, path, and other details about that certificate that are not editable. You can enter an alphanumeric name for the certificate in Identifier if you want to rename the certificate. You can use underscore (_) and or dash (-) characters in the name.
View/Download Certificate opens a window with the certificate string. Use the clipboard icon to copy the certificate to the clipboard or Download to download the certificate to your server. Keep the certificate in a secure area where you can back up and save it.
View/Download Key opens a window with the certificate private key. Use the clipboard icon to copy the public key to the clipboard or Download to download the key to your server. Keep the private key in a secure area where you can back up and save it.