TrueNAS Documentation Archive
This content follows the TrueNAS 23.10 (Cobia) releases. Archival documentation is provided for reference only and not actively maintained. Use the Product and Version selectors above to view content specific to different TrueNAS software or major version.
Using Rootless Login
4 minute read.
Last Modified 2024-03-19 08:38 EDTThe initial implementation of TrueNAS SCALE rootless log in permits users to use the root user but encourages users to create the local administrator account when first installing SCALE.
Starting with SCALE Bluefin 22.12.0, root account logins are deprecated for security hardening and to comply with Federal Information Processing Standards (FIPS). All TrueNAS users should create a local administrator account with all required permissions and begin using it to access TrueNAS. When the root user password is disabled, only an administrative user account can log in to the TrueNAS web interface.
TrueNAS SCALE plans to permanently disable root account access in a future release.
If migrating from CORE to SCALE, when first logging into SCALE as the root user, you are advised to create the administrator account. All users should create the local administrator account and use this account for web interface access. To improve system security after the local administrator account is created, disable the root account password so that root access to the system is restricted.
Some UI screens and settings still refer to the root account, but these references are updating to the administrator account in future release of SCALE.
At present, SCALE has both the root and local administrator user logins and passwords. If properly set up, the local administrator (admin) account performs the same functions and has the same access the root user has.
The root user is no longer the default user so you must add and enable a password to use the root user.
As a security measure, the root user password is disabled when you create the admin user during installation. Do not disable the admin account and root passwords at the same time. If both root and admin account passwords become disabled at the same time and the web interface session times out, a one-time sign-in screen allows access to the system.
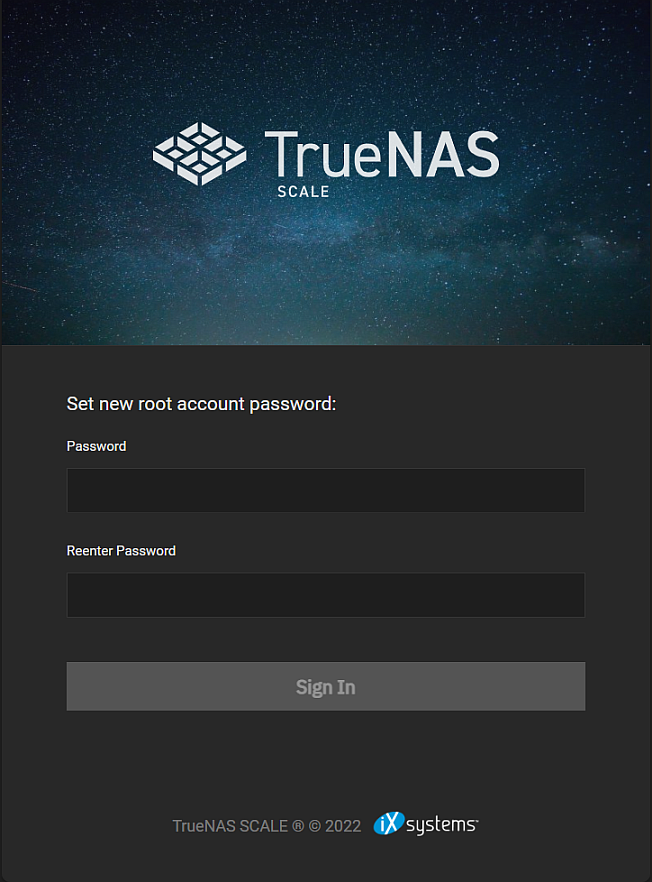
Enter and confirm a password to gain access to the UI. After logging in, immediately go to Credentials > Local Users to enable either the root or admin password before the session times out again. This temporary password is not saved as a new password and it does not enable the admin or root passwords, it only provides one-time access to the UI.
When disabling a password for UI login, it is also disabled for SSH access.
To enable SSH to access the system as root or the admin user:
Configure the SSH service.
a. Go to System Settings > Services, then select Configure for the SSH service.
b. Select Log in as Root with Password to enable the root user to sign in as root.
Select Log in as Admin with Password and Allow Password Authentication to enable the admin user to sign in as admin. Select both options.
c. Click Save and restart the SSH service.
Configure or verify the user configuration options to allow ssh access.
If you want to SSH into the system as the root, you must create and enable a password for the root user. If the root password password is disabled in the UI you cannot use it to gain SSH access to the system.
To allow the admin user to issue commands in an ssh session, edit the admin user and select which sudo options are allowed.
Select Allow all sudo commands with no password. You might see a prompt in the ssh session to enter a password the first time you enter a sudo command but will not see this password prompt again in the same session.
To use two-factor authentication with the administrator account (root or admin user), first configure and enable SSH service to allow SSH access, then configure two-factor authentication. If you have the root user configured with a password and enable it, you can SSH into the system with the root user. Security best practice is to disable the root user password and only use the local administrator account.
At present, rootless log in works with TrueCommand but you need to set up and use an API key. Future releases of TrueCommand should eliminate the need for the API key.



