TrueNAS CORE Version Documentation
This content follows the TrueNAS CORE 13.0 releases. Use the Product and Version selectors above to view content specific to different TrueNAS software or major version.
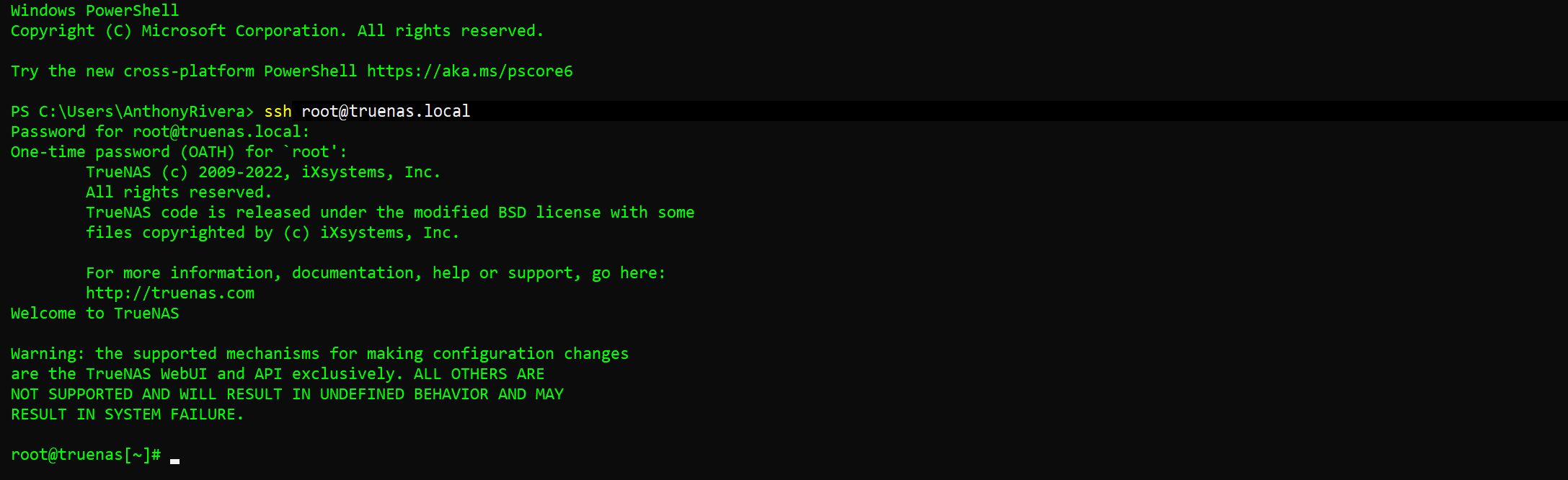
Using Two-Factor Authentication
2 minute read.
We recommend two-factor authentication (2FA) for increased security. TrueNAS offers 2FA to ensure that a compromised administrator (root) password alone cannot grant access to the administrator interface. To utilize 2FA, you need a mobile device with Google Authenticator installed. Other authenticator applications can be used, but you will need to confirm the settings and QR codes generated in TrueNAS are compatible with your particular app before permanently activating 2FA.