TrueCommand Version Documentation
This content follows TrueCommand 3.0 releases. Use the Product and Version selectors above to view content specific to TrueNAS software or major versions.
Administration
10 minute read.
Last Modified 2024-03-19 09:20 EDTThe Administration screen, available to users with administrator permissions, displays additional system details and offers a variety of TrueCommand configuration options through the system widgets or information cards.
To access the Administration screen, click the gear settings icon at the top right of the screen to open the settings menu, then click Administration.
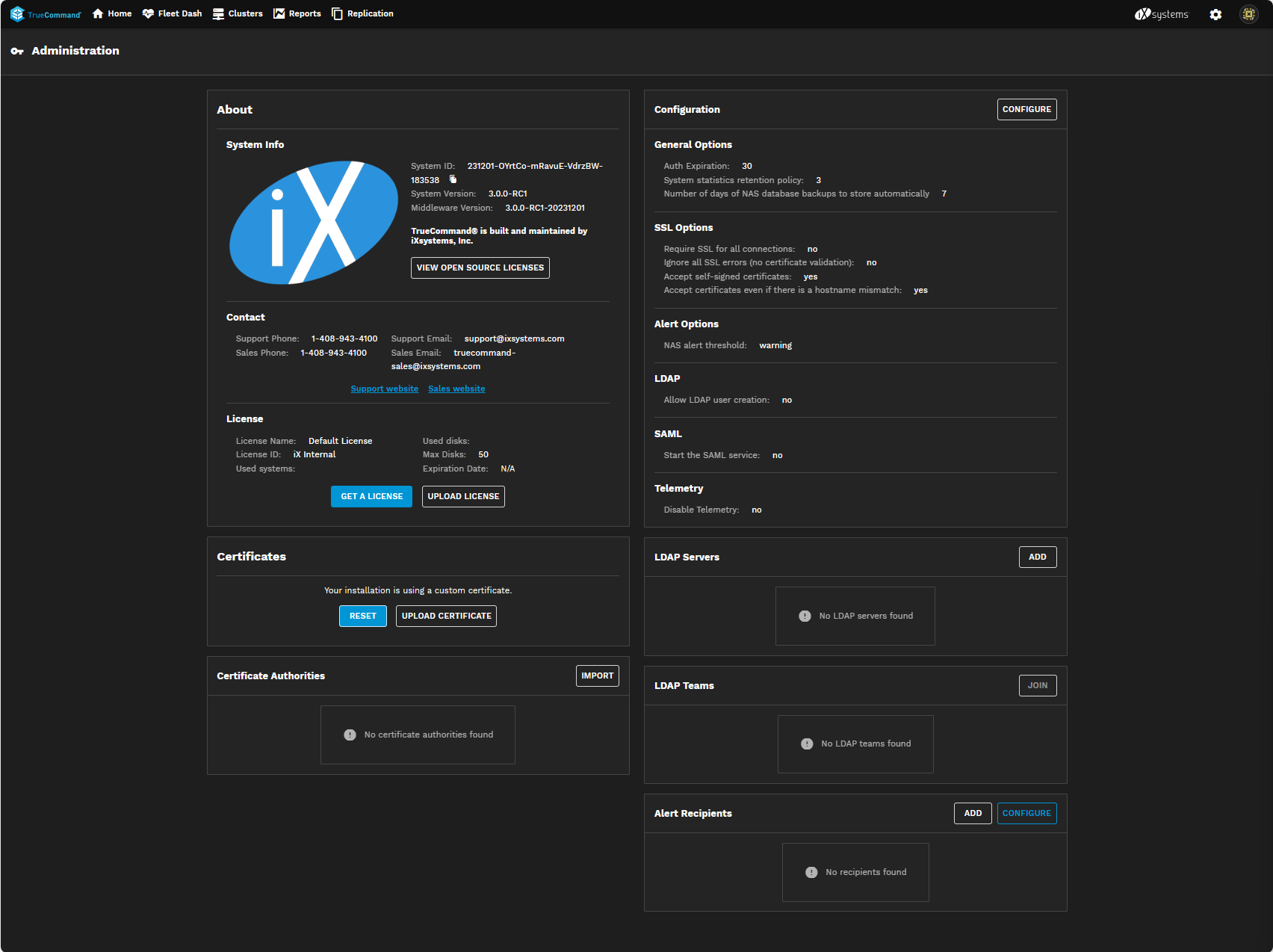
The screen has seven widgets:
- About - Shows TrueCommand system information, iXsystems Support Contact information, and TrueCommand licenses.
- Certificates - Allows you to upload or reset certificates.
- Certificate Authorities - Allows you import certificate authorities into TrueCommand.
- Configuration - Provides access to general, SSL, alert, LDAP and SAML service, and Telemetry settings.
- LDAP Servers - Allows you to add an LDAP server.
- LDAP Teams - Allows you to join LDAP teams.
- Alert Recipients - Allows you to configure alert recipient users emails and configure mailing list email settings.
The About widget displays the current TrueCommand system ID and version, iXsystems Support contact information, and license details.
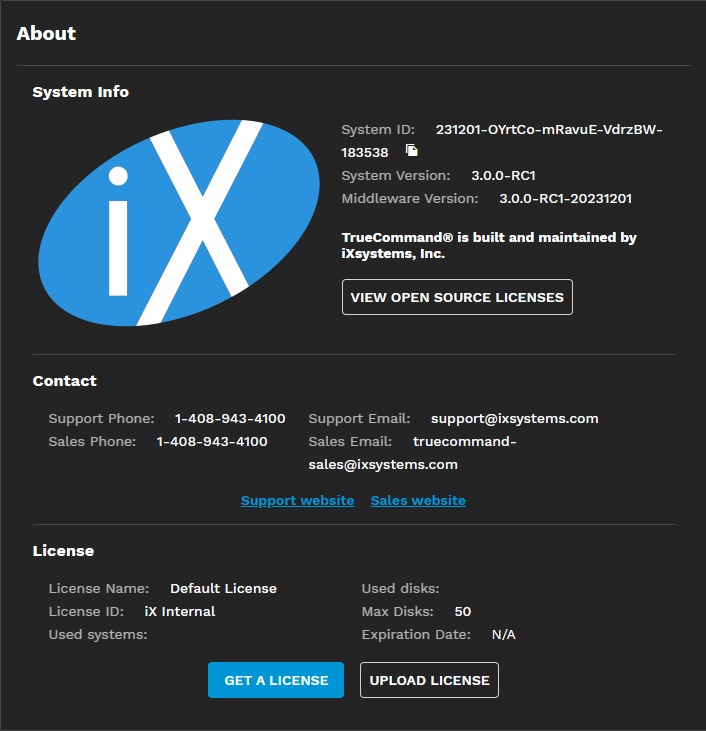
Click View Open Source Licenses to see a list of open-source licenses TrueCommand uses.
You can expand TrueCommand to monitor more disks by upgrading or purchasing a license from iXsystems. Click GET A LICENSE to open a new browser tab to purchase a TrueCommand license. You can also contact iXsystems to upgrade the current license.
After you upgrade or purchase a new license, upload it to TrueCommand. Click Browse to open a file browser on your local system. Select the new license file to upload and click UPLOAD LICENSE to apply the new license to TrueCommand.
The Certificates widget shows the certificates TrueCommand uses and has options to reset or upload a certificate.
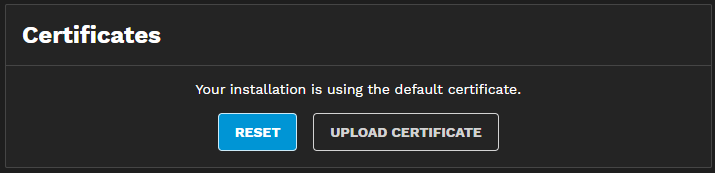
Click Upload Certificate to open the Upload Certificate screen, where you can either browse to or drag and drop a certificate and a private key file into TrueCommand.
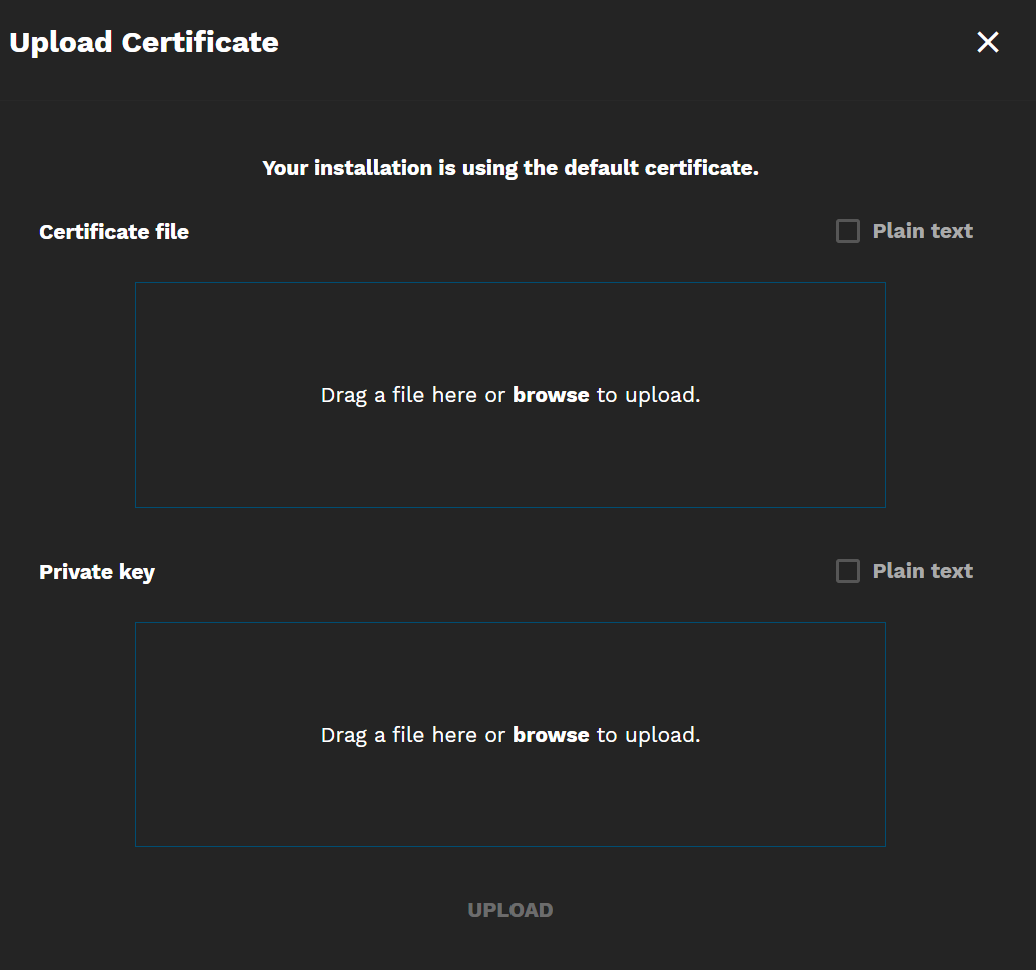
Selecting Plain text allows you to copy and paste the raw text instead of uploading a file.
Click IMPORT in the Certificate Authorities widget to add a certificate authority (CA) to TrueCommand.
Click Import to open the Add Certificate Authority screen, where you enter the name for the CA and either browse to or drag and drop the CA file into TrueCommand.
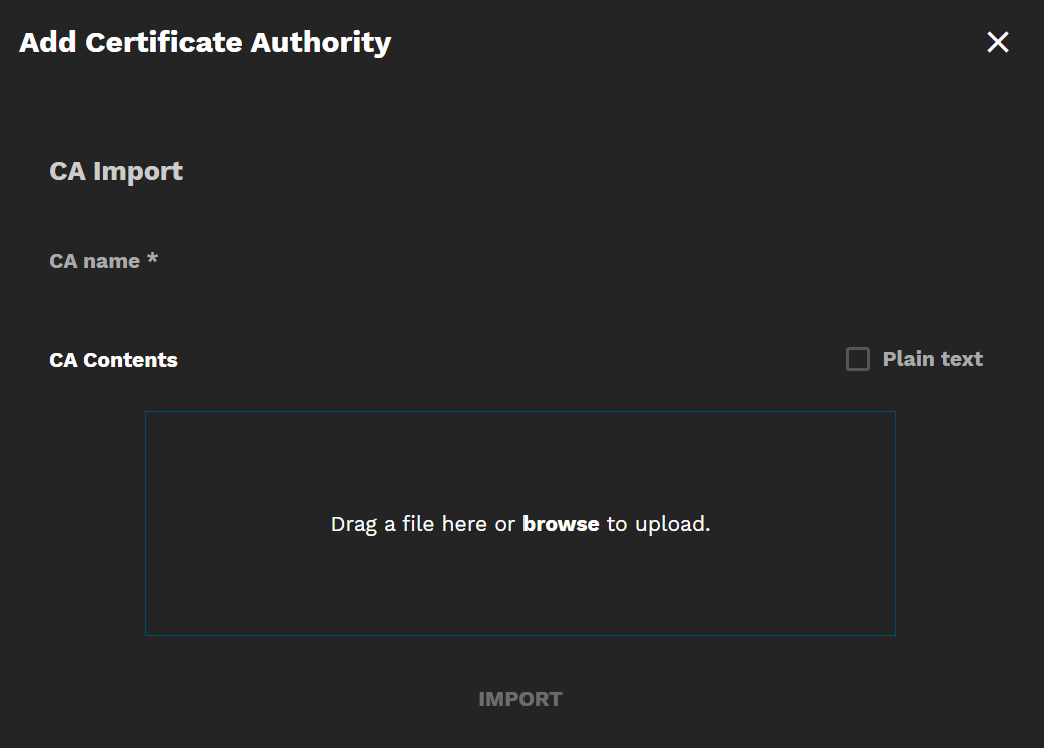
Selecting Plain Text allows you to copy and paste the raw text before you upload it.
The Configuration widget displays current general, SSL, alert options, LDAP, SAML, and telemetry service settings. It provides access to a configuration screen to add or make changes to these settings:
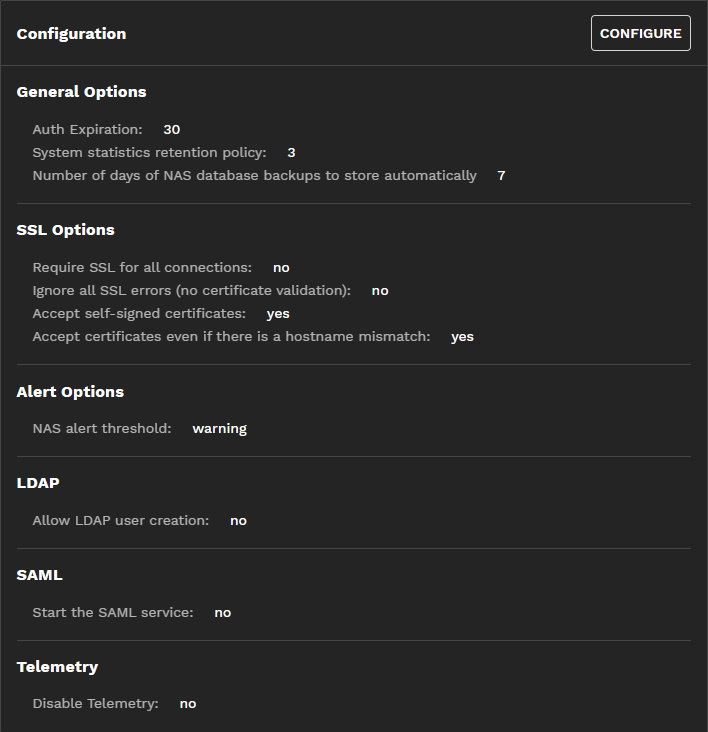
Click CONFIGURE to open the Configuration screen where you can manage feature settings. After changing any options, click Save or Cancel to reset fields back to their previous values.
General options include settings for account sessions, how long TrueCommand stores system statistics and the number of TrueNAS configuration file backups to store.
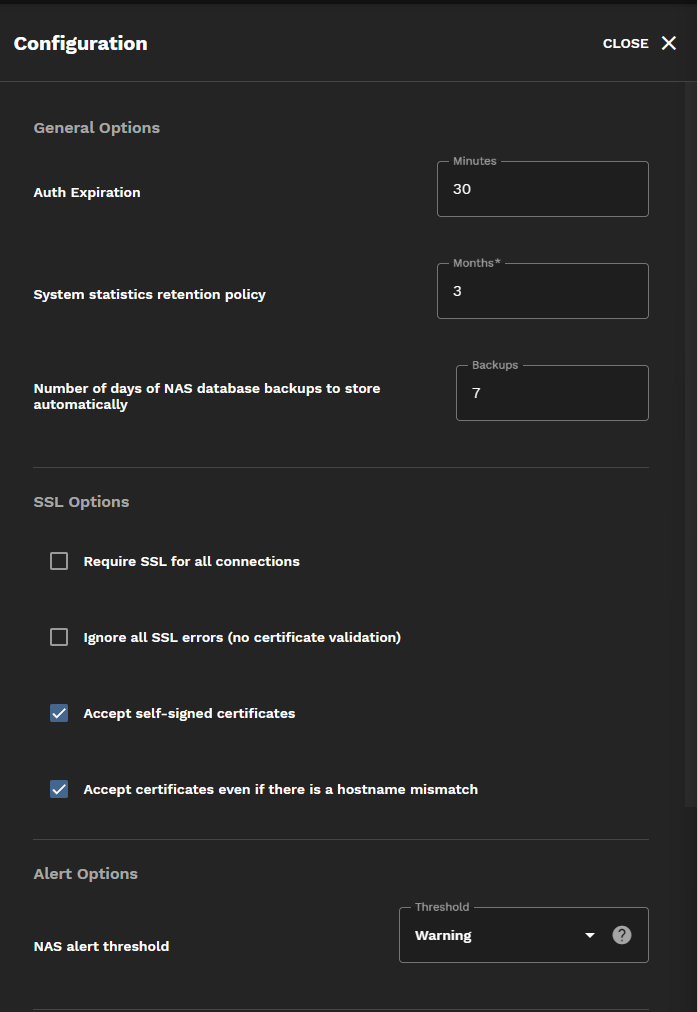
By default, TrueCommand logs out idle user account sessions after 30 minutes of inactivity. A warning shows when the session is within 3 minutes of timing out. Update the Minutes field to set a different number of minutes before an idle user account is automatically logged out. Setting 0 disables automatic logouts.
TrueCommand stores 3 months of statistics from connected TrueNAS systems and 7 days of TrueNAS database backups. Enter numeric values in the Months and Backups fields to change these defaults.
This feature is only available for local installations or containerized TrueCommand deployments.
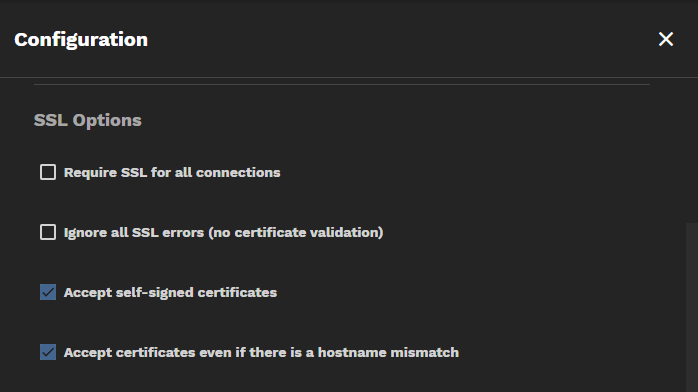
By default, TrueCommand attempts an SSL connection, then a non-SSL connection if the first attempt fails. You can disable non-SSL connection attempts by setting Require SSL for all connections, which is useful when a monitored system uses a custom port or does not allow SSL-secured access.
There are additional options to configure how TrueCommand handles certificates. By default, TrueCommand accepts self-signed certificates and certificate host name mismatches. Self-signed certificates enable the first-time login to TrueCommand. Accept certificate even if there is a hostname mismatch allows TrueCommand to accept certificates from systems that use a host name, even though it registered them with an IP address (or vice-versa).
You can adjust the alert levels that TrueCommand shows from a connected TrueNAS system to tune the system messages displayed according to your use case. Select an alert category to ignore. Options are None, Information, Warning and Critical. Alerts generated by TrueCommand rules are unaffected.
The Allow LDAP user creation checkbox is not selected (disabled) by default. When disabled, you can use LDAP to log in with existing users.
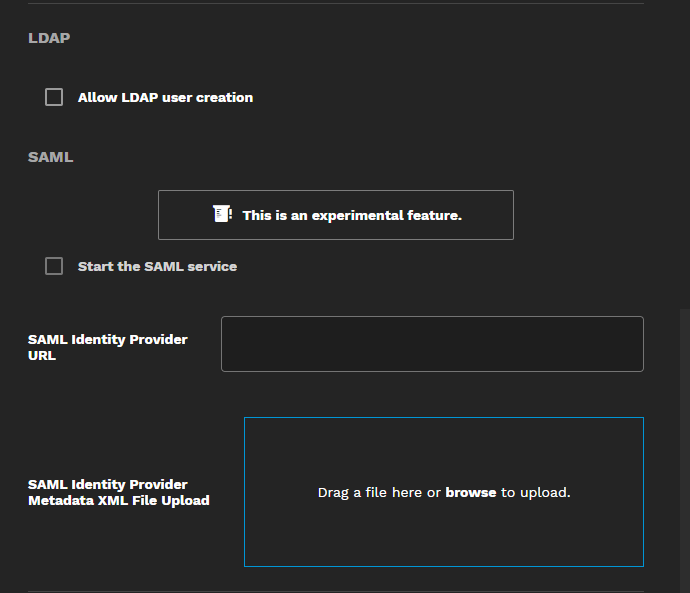
The SAML service is an experimental feature that allows users to configure TrueCommand SAML for Active Directory or Google Admin.
TrueCommand reports some anonymous basic usage telemetry to iXsystems for product improvement analysis.
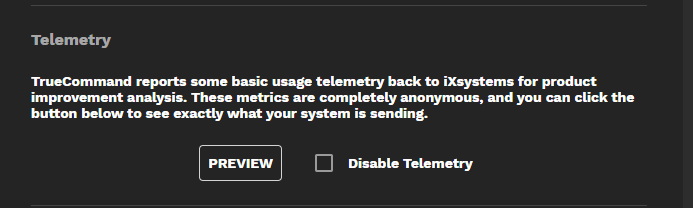
Click the PREVIEW button to see what your system is sending.
Select Disable Telemetry to deny telemetry collection.
Users can configure TrueCommand to use LDAP servers for security and authentication management among connected TrueNAS systems.
TrueCommand supports using LDAP to better integrate within an established network environment. LDAP/AD allows using single sign-on credentials from the Lightweight Directory Access Protocol (LDAP) or Active Directory (AD). Users can log in with an LDAP or AD account without creating a separate TrueCommand login.
LDAP and AD require the server IP address or DNS hostname and domain to use. The LDAP or AD Username (optional) is required when the TrueCommand user name does not match the LDAP or AD credentials.
Click on the settings (Gear) > Administration.
Click Add on the LDAP Servers widget to open the Add LDAP Server configuration screen.
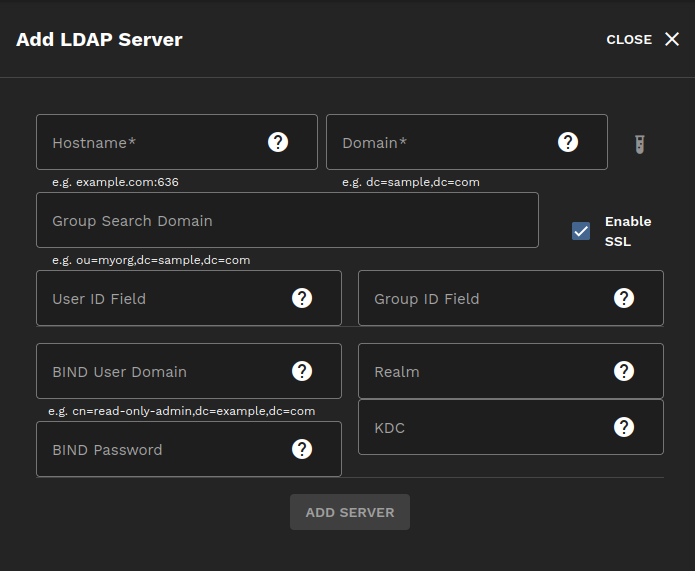
To configure LDAP, type the LDAP server IP address or DNS host name into the LDAP Server URL field, type the domain name in the Domain field, and click ADD SERVER. You can add multiple LDAP servers and domains.
Click on the Test LDAP Config icon to open a window that allows you to test your connection to the LDAP server. The Remove LDAP Server icon removes the selected LDAP server.
TrueCommand supports two methods of validating LDAP user credentials:
The direct BIND method uses the Domain and User ID Field values to create a static domain string for user authentication.
Example:
- Domain: dc=mycorp,dc=com
- User ID Field: uid
When bobby.singer attempts to log in, TrueCommand establishes an SSL-secure connection to the LDAP server and attempts to bind with the static domain uid=bobby.singer,dc=mycorp,dc=com and the user-provided password. If successful, the user authentication verifies, and Bobby Singer may access TrueCommand.
The indirect BIND authentication method is more dynamic and searches for the proper user domain settings rather than making format assumptions. With TrueCommand, indirect BIND configures a bind user (typically a read-only, minimal-permissions user account) with a known domain/password to perform the initial bind to the LDAP server. After logging in, TrueCommand searches for the user domain requesting to log in. It then attempts a second bind with the user domain and provided password.
Example:
- Domain: dc=mycorp,dc=com
- User ID Field: uid
- BIND User Domain: uid=binduser,cn=read-only-bind,dc=mycorp,dc=com
- BIND Password: pre-shared-key
When bobby.singer attempts to log in, TrueCommand establishes an SSL-secure connection to the LDAP server. TrueCommand uses the BIND User Domain and BIND Password settings to perform an initial bind using pre-known settings from your LDAP provider. When bound, TrueCommand searches for the user matching uid=bobby.singer, but only within the subdomains that include the domain setting (dc=mycorp,dc=com in this example). If TrueCommand finds a user, it uses the entire user domain string from the search result to initialize a second bind along with the user-provided password. If successful, TrueCommand verifies the user authentication, and Bobby Singer is allowed access to TrueCommand.
If the LDAP server uses an SSL certificate generated by a custom certificate authority (CA), then one of two things must occur before TrueCommand can use the LDAP server. Either:AD/LDAP authentication requires SSL connections.
Users must register the custom certificate authority with TrueCommand via the Certificates tab on the Administration screen.
Or
Users can disable the Verify SSL option to accept whatever SSL certificate the server provides. Users might need to choose this if the LDAP server host name differs from the one listed on the certificate or if the server uses a self-signed SSL certificate.
Selecting Allow LDAP user creation means TrueCommand creates user accounts when someone logs in to the User Interface with their LDAP credentials. JOIN TEAM automatically adds LDAP users to specific TrueCommand teams.
The LDAP Teams widget allows you to add TrueCommand teams to your LDAP server by clicking JOIN and selecting a team from the list.
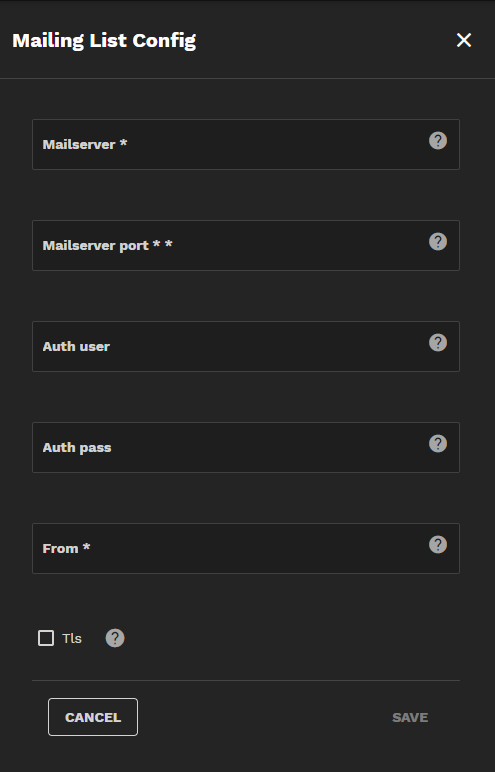
The Alert Recipients widget allows you to add recipient email addresses and configure mail list settings.
Click Add to open the Add Recipient screen, where you can add an email address to your LDAP server.
Click Configure to open the Mailing List Configure screen.
- SAML Tutorials: Provides SAML tutorials for TrueCommand SAML configurations.
- Configuring TrueCommand SAML Service for Active Directory: Provides detailed instructions on setting up SAML service in TrueCommand and Active Directory.
- Configuring TrueCommand SAML Service for Google Admin: Provides detailed instructions on setting up SAML service in TrueCommand and Google Admin.
- Configuring IDP SAML as SSO for TrueCommand SAML Service: Provides information on setting up an identity provider (IDP) SAML provider as SSO for TrueCommand SAML service.
- LDAP Servers: Describes how to configure LDAP servers for TrueCommand.

